A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015.
“It can also deliver ‘add-on packages’ such as additional malicious payloads, benign decoy documents, and executables,” cybersecurity firm Secureworks said in a Wednesday report. “It features robust anti-analysis and anti-tamper controls that can make detection, analysis, and eradication challenging.”
Malware delivered by the crypter includes information steakers and remote access trojans (RATs) such as Agent Tesla, AsyncRat, NanoCore, and RedLine Stealer. “DarkTortilla has versatility that similar malware does not,” the researchers noted.

Crypters are software tools that use a combination of encryption, obfuscation, and code manipulation of malware so as to bypass detection by security solutions.
The delivery of DarkTortilla occurs via malicious spam emails which contain archives with an executable for an initial loader that’s used to decode and launch a core processor module either embedded within itself or fetched from text storage sites such as Pastebin.
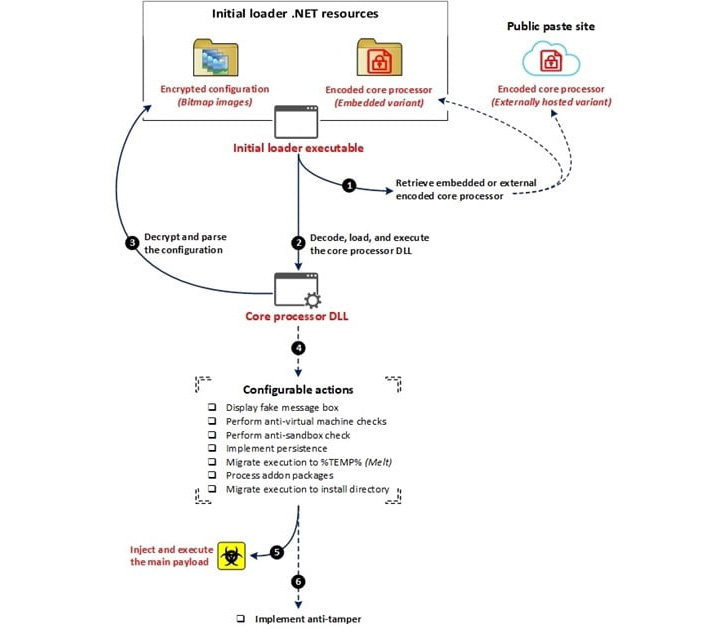
The core processor is then responsible for establishing persistence and injecting the primary RAT payload into memory without leaving a trail on the file system through an elaborate configuration file that also allows it to drop add-on packages, including keyloggers, clipboard stealers, and cryptocurrency miners.
DarkTortilla is further noteworthy for its use of anti-tamper controls that ensure both the processes used to execute the components in memory are immediately rerun upon termination.
Specifically, the persistence of the initial loader is achieved by means of a second executable referred to as a WatchDog that’s designed to keep tabs on the designated process and rerun it should it be killed.

This technique is reminiscent of a similar mechanism adopted by a threat actor called Moses Staff, which, earlier this year, was found relying on a watchdog-based approach to prevent any interruption to its payloads. Also employed are two other controls to guarantee the continued execution of the dropped WatchDog executable itself and the persistence for the initial loader.
Secureworks said it identified an average of 93 unique DarkTortilla samples being uploaded to the VirusTotal malware database per week over a 17-month period from January 2021 to May 2022. Of all the 10,000 samples tracked during the timeframe, only just about nine of them were used to spread ransomware – seven delivering Babuk and two others administering MedusaLocker.
“DarkTortilla is capable of evading detection, is highly configurable, and delivers a wide range of popular and effective malware,” the researchers concluded. “Its capabilities and prevalence make it a formidable threat.”
That said, the exact modus operandi of how the crypter reaches the hands of the threat actors remains unclear, although it’s suspected that it may be peddled on the criminal underground as a service.
“Despite scouring underground marketplaces and forums, we’ve been unable to find where or how DarkTortilla is being sold,” Rob Pantazopoulos, senior security researcher at Secureworks Counter Threat Unit (CTU), told The Hacker News.
“We did encounter another crypter being advertised named PureCrypter, which isn’t DarkTortilla but exhibits many of the same. Given the similarities we suspect that it’s operating in the same market; meaning it is likely opportunistic and being sold to anyone willing to pay a reasonable fee.”
