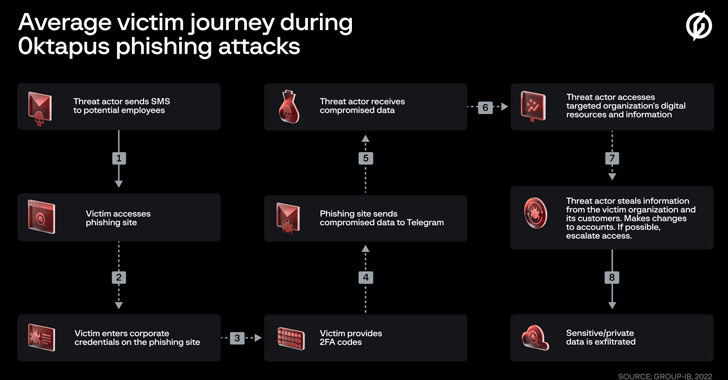
The threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing campaign aimed at 136 organizations that resulted in a cumulative compromise of 9,931 accounts.
The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to “obtain Okta identity credentials and two-factor authentication (2FA) codes from users of the targeted organizations.”
Calling the attacks well designed and executed, the Singapore-headquartered company said the adversary singled out employees of companies that are customers of identity services provider Okta.

The modus operandi involved sending targets text messages containing links to phishing sites that impersonated the Okta authentication page of the respective targeted entities.
“This case is of interest because despite using low-skill methods it was able to compromise a large number of well-known organizations,” Group-IB said. “Furthermore, once the attackers compromised an organization they were quickly able to pivot and launch subsequent supply chain attacks, indicating that the attack was planned carefully in advance.”
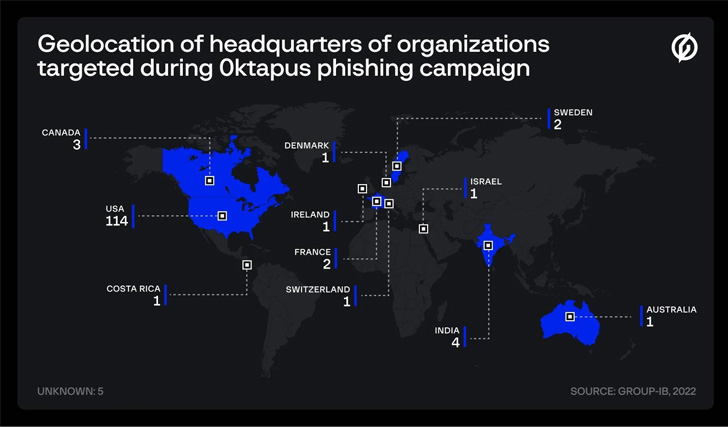
At least 169 unique phishing domains are said to have been set up for this purpose, with victim organizations primarily located in the U.S. (114), India (4), Canada (3), France (2), Sweden (2), and Australia (1), among others. These websites were united by the fact that they made use of a previously undocumented phishing kit.
A majority of the affected organizations are software companies, followed by those belonging to telecom, business services, finance, education, retail, and logistics sectors.
What’s notable about the attacks is the use of an actor-controlled Telegram channel to drop the compromised information, which included user credentials, email addresses, and multi-factor authentication (MFA) codes.
Group-IB said it was able to link one of the channel administrators, who goes by the alias X, to a Twitter and a GitHub account that suggests the individual may be based in the U.S. state of North Carolina.

The ultimate objectives of the campaign remain unclear, but it’s suspected to be espionage and financially motivated, enabling the threat actor to access confidential data, intellectual property, and corporate inboxes, as well as siphon funds.
On top of that, the attempts to hack into Signal accounts imply that the attackers are also trying to get hold of private conversations and other sensitive data. It’s still not known how the hackers obtained phone numbers and the names of employees.
“While the threat actor may have been lucky in their attacks it is far more likely that they carefully planned their phishing campaign to launch sophisticated supply chain attacks,” Group-IB analyst Roberto Martinez said.
“It is not yet clear if the attacks were planned end-to-end in advance or whether opportunistic actions were taken at each stage. Regardless, the 0ktapus campaign has been incredibly successful, and the full scale of it may not be known for some time.”