The threat actor behind the SolarWinds supply chain attack has been linked to yet another “highly targeted” post-exploitation malware that could be used to maintain persistent access to compromised environments.
Dubbed MagicWeb by Microsoft’s threat intelligence teams, the development reiterates Nobelium’s commitment to developing and maintaining purpose-built capabilities.
Nobelium is the tech giant’s moniker for a cluster of activities that came to light with the sophisticated attack targeting SolarWinds in December 2020, and which overlaps with the Russian nation-state hacking group widely known as APT29, Cozy Bear, or The Dukes.

“Nobelium remains highly active, executing multiple campaigns in parallel targeting government organizations, non-governmental organizations (NGOs), intergovernmental organizations (IGOs), and think tanks across the US, Europe, and Central Asia,” Microsoft said.
MagicWeb, which shares similarities with another tool called FoggyWeb, is assessed to have been deployed to maintain access and preempt eviction during remediation efforts, but only after obtaining highly privileged access to an environment and moving laterally to an AD FS server.
While FoggyWeb comes with specialized capabilities to deliver additional payloads and steal sensitive information from Active Directory Federation Services (AD FS) servers, MagicWeb is a rogue DLL (a backdoored version of “Microsoft.IdentityServer.Diagnostics.dll”) that facilitates covert access to an AD FS system through an authentication bypass.
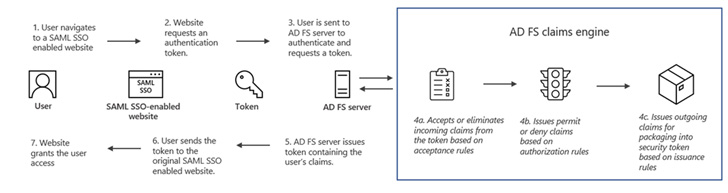
“Nobelium’s ability to deploy MagicWeb hinged on having access to highly privileged credentials that had administrative access to the AD FS servers, giving them the ability to perform whatever malicious activities they wanted to on the systems they had access to,” Microsoft said.
The findings come on the heels of the disclosure of an APT29-led campaign aimed at NATO-affiliated organizations with the goal of accessing foreign policy information.

Specifically, this entails disabling an enterprise logging feature called Purview Audit (previously Advanced Audit) to harvest emails from Microsoft 365 accounts.”APT29 continues to demonstrate exceptional operational security and evasion tactics,” Mandiant said.
Another newer tactic used by the actor in recent operations is the use of a password guessing attack to obtain the credentials associated with a dormant account and enroll it for multi-factor authentication, granting it access to the organization’s VPN infrastructure.
APT29 remains a prolific threat group just as it’s skillful. Last month, Palo Alto Networks Unit 42 flagged a phishing campaign that takes advantage of Dropbox and Google Drive cloud storage services for malware deployment and other post-compromise actions.
