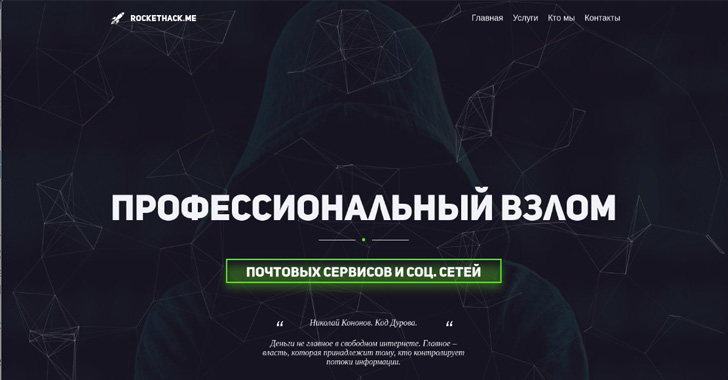
A hack-for-hire group that was first exposed in 2019 has expanded its focus to set its sights on entities with business or political ties to Russia.
Dubbed Void Balaur, the cyber mercenary collective has a history of launching cyberattacks against biotechnology and telecom companies since 2015. As many as 3,500 victims have been reported as of November 2021.
“Void Balaur […] primarily dabbles in cyber espionage and data theft, selling the stolen information to anyone willing to pay,” Trend Micro noted at the time.

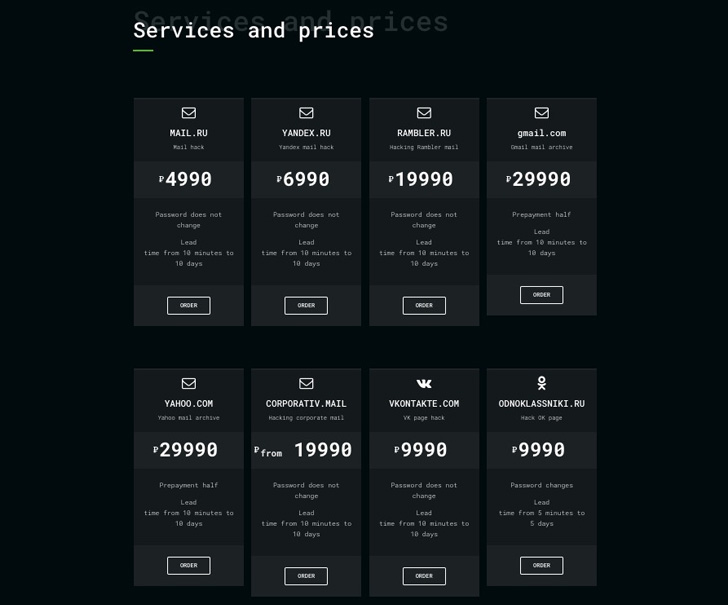
Attacks conducted by the group are typically both generic and opportunistic and are aimed at gaining unauthorized access to widely-used email services, social media, messaging, and corporate accounts.
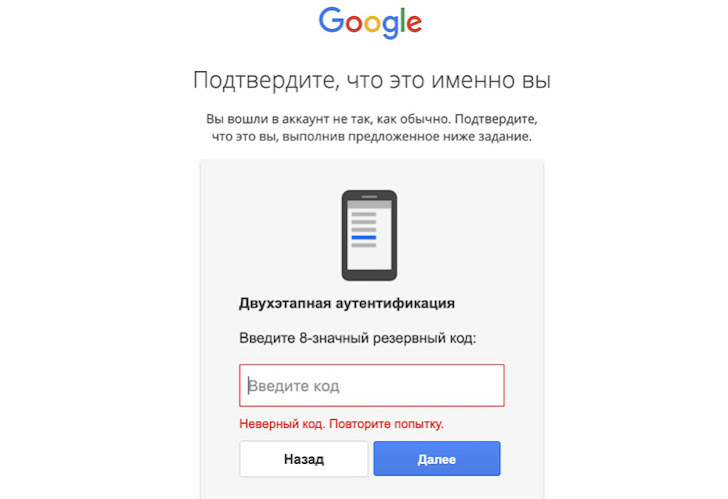
Earlier this June, Google’s Threat Analysis Group (TAG) took the wraps off a set of credential theft attacks targeting journalists, European politicians, and non-profit’s mounted by the threat actor.
“Void Balaur also goes after targets valuable for prepositioning or facilitating future attacks, SentinelOne researcher Tom Hegel said, adding the targets span Russia, the U.S., the U.K., Taiwan, Brazil, Kazakhstan, Ukraine, Moldova, Georgia, Spain, Central African Republic, and Sudan.
The hack-for-hire service offering linked to the group is said to be advertised under different personas, such as Hacknet and RocketHack. Over the years, the operators have provided other services, including remote access to devices, SMS records, and real-time location tracking.
What’s more, the attack infrastructure operated by Void Balaur encompasses more than 5,000 unique domains that claim to be email websites, authentication services, and public services portals.

But in what appears to be an operational oversight, one of the domains controlled by the group (accounts-my-mail-gmail[.]com) resolved to an IP address that’s owned and operated by the Russian Federal Guard Service (FSO) in early 2022, suggesting a potential connection.
Although Void Balaur’s attacks are aimed at individuals and organizations across the world, campaigns mounted in 2022 have singled out people that are involved in business and political situations that are of interest to Russia.
Also prevalent is the use of highly reproducible phishing emails that mimic local government services or banks to trick targets into providing their account credentials upon clicking a malicious link.
“Void Balaur remains a highly active and evolving threat to individuals across the globe. From the targeting of well known email services to the offering of hacking corporate networks, the group represents a clear example of the hack-for-hire marketm,” Hegel said.