A “highly operational, destructive, and sophisticated nation-state activity group” with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022.
Microsoft’s threat intelligence teams, alongside LinkedIn Threat Prevention and Defense, attributed the intrusions with high confidence to Zinc, which is also tracked under the names Labyrinth Chollima.
Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.

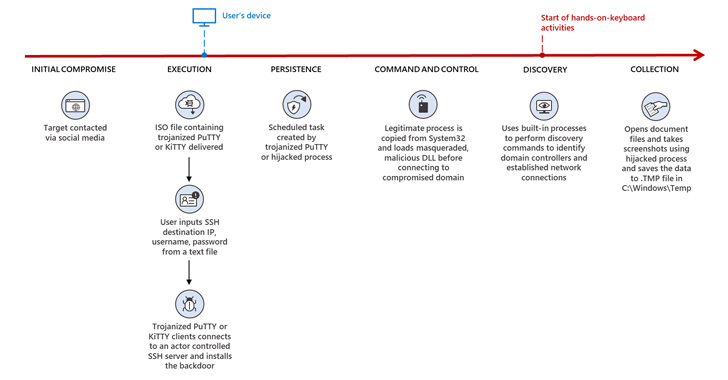
The tech giant said it observed Zinc leveraging a “wide range of open-source software including PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software installer for these attacks.”
According to CrowdStrike, Zinc “has been active since 2009 in operations aimed at collecting political, military, and economic intelligence on North Korea’s foreign adversaries and conducting currency generation campaigns.”
The latest findings dovetail with a recent report from Google-owned Mandiant, which uncovered the adversary’s use of PuTTY via fraudulent job lures shared with potential targets on LinkedIn as part of a campaign dubbed Operation Dream Job.
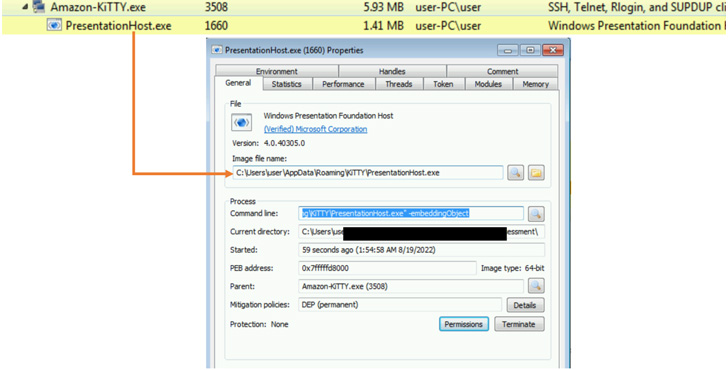
This involves establishing initial connections with individuals by posing as recruitment professionals as a trust-building exercise, before moving the conversation to WhatsApp, where a tailored lure document or seemingly benign software is shared, effectively activating the infection sequence.
A successful compromise is followed by the threat actor moving laterally across the network and exfiltrating collected information of interest by deploying a backdoor called ZetaNile (aka BLINDINGCAN OR AIRDRY).

But in a bid to evade security defenses and avoid raising red flags, the implant is downloaded only when the victim uses the SSH clients to connect to a particular IP address through the credentials specified in a separate text file.
Likewise, attacks employing the trojanized version of TightVNC Viewer are configured to install the backdoor only when the user selects a particular remote host from the options provided.
“Zinc attacks appear to be motivated by traditional cyberespionage, theft of personal and corporate data, financial gain, and corporate network destruction,” the company said.
“Zinc attacks bear many hallmarks of state-sponsored activities, such as heightened operational security, sophisticated malware that evolves over time, and politically motivated targeting.”