A threat actor likely with associations to China has been attributed to a new supply chain attack that involves the use of a trojanized installer for the Comm100 Live Chat application to distribute a JavaScript backdoor.
Cybersecurity firm CrowdStrike said the attack made use of a signed Comm100 desktop agent app for Windows that was downloadable from the company’s website.
The scale of the attack is currently unknown, but the trojanized file is said to have been identified at organizations in the industrial, healthcare, technology, manufacturing, insurance, and telecom sectors in North America and Europe.
Comm100 is a Canadian provider of live audio/video chat and customer engagement software for enterprises. It claims to have more than 15,000 customers across 51 countries.

“The installer was signed on September 26, 2022 at 14:54:00 UTC using a valid Comm100 Network Corporation certificate,” the company noted, adding it remained available until September 29.
Embedded within the weaponized executable is a JavaScript-based implant that executes a second-stage JavaScript code hosted on a remote server, which is designed to provide the actor with surreptitious remote shell functionality.
Also deployed as part of the post-exploitation activity is a malicious loader DLL named MidlrtMd.dll that launches an in-memory shellcode to inject an embedded payload into a new Notepad process.
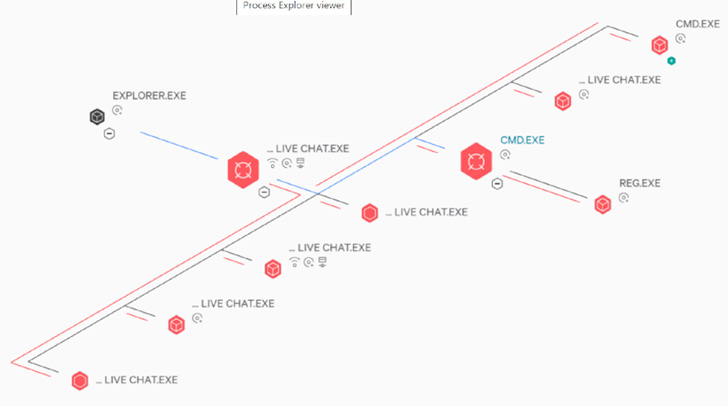
Supply chain compromises, like that of SolarWinds and Kaseya, are becoming an increasingly lucrative strategy for threat actors to target a widely-used software provider to gain a foothold in the networks of downstream customers.
As of writing, none of the security vendors flag the installer as malicious. Following responsible disclosure, the issue has since been addressed with the release of an updated installer (10.0.9).

CrowdStrike has tied the attack with moderate confidence to an actor with a China nexus based on the presence of Chinese-language comments in the malware and the targeting of online gambling entities in East and Southeast Asia, an already established area of interest for China-based intrusion actors.
That said, the payload delivered in this activity differs from other malware families previously identified as operated by the group, suggesting an expansion to its offensive arsenal.
The name of the adversary was not disclosed by CrowdStrike, but the TTPs point in the direction of a threat actor called Earth Berberoka (aka GamblingPuppet), which earlier this year was found using a fake chat app called MiMi in its attacks against the gambling industry.
