The China-aligned espionage-focused actor dubbed Winnti has set its sights on government organizations in Hong Kong as part of an ongoing campaign dubbed Operation CuckooBees.
Active since at least 2007, Winnti (aka APT41, Barium, Bronze Atlas, and Wicked Panda) is the name designated to a prolific cyber threat group that carries out Chinese state-sponsored espionage activity, predominantly aimed at stealing intellectual property from organizations in developed economies.
The threat actor’s campaigns have targeted healthcare, telecoms, high-tech, media, agriculture, and education sectors, with infection chains primarily relying on spear-phishing emails with attachments to initially break into the victims’ networks.
Earlier this May, Cybereason disclosed long-running attacks orchestrated by the group since 2019 to siphon technology secrets from technology and manufacturing companies mainly located in East Asia, Western Europe, and North America.

The intrusions, clubbed under the moniker Operation CuckooBees, are estimated to have resulted in the exfiltration of “hundreds of gigabytes of information,” the Israeli cybersecurity company revealed.
The latest activity, according to the Symantec Threat Hunter team, part of Broadcom Software, is a continuation of the proprietary data theft campaign, but with a focus on Hong Kong.
The attackers remained active on some of the compromised networks for as long as a year, the company said in a report shared with The Hacker News, adding the intrusions paved the way for the deployment of a malware loader called Spyder, which first came to light in March 2021.
“[Spyder] is being used for targeted attacks on information storage systems, collecting information about corrupted devices, executing mischievous payloads, coordinating script execution, and C&C server communication,” the SonicWall Capture Labs Threat Research Team noted at the time.
Also deployed alongside Spyder were other post-exploitation tools, such as Mimikatz and a trojanized zlib DLL module that’s capable of receiving commands from a remote server or loading an arbitrary payload.
Symantec said that it did not observe the delivery of any final-stage malware, although the motives of the campaign are suspected to be linked to intelligence gathering based on tactical overlaps with previous attacks.
“The fact that this campaign has been ongoing for several years, with different variants of the Spyder Loader malware deployed in that time, indicates that the actors behind this activity are persistent and focused adversaries, with the ability to carry out stealthy operations on victim networks over a long period of time,” Symantec said.
Winnti targets Sri Lankan government entities
As a further sign of Winnti’s sophistication, Malwarebytes uncovered a separate set of attacks targeting government entities in Sri Lanka in early August with a new backdoor referred to as DBoxAgent that leverages Dropbox for command-and-control.
“To our knowledge, Winnti (a China-backed APT) is targeting Sri Lanka for the first time,” the Malwarebytes Threat Intelligence team said.

The killchain is also notable for making use of an ISO image hosted on Google Drive that purports to be a document containing information about economic assistance, indicating an attempt by the threat actor to capitalize on the ongoing economic crisis in the nation.
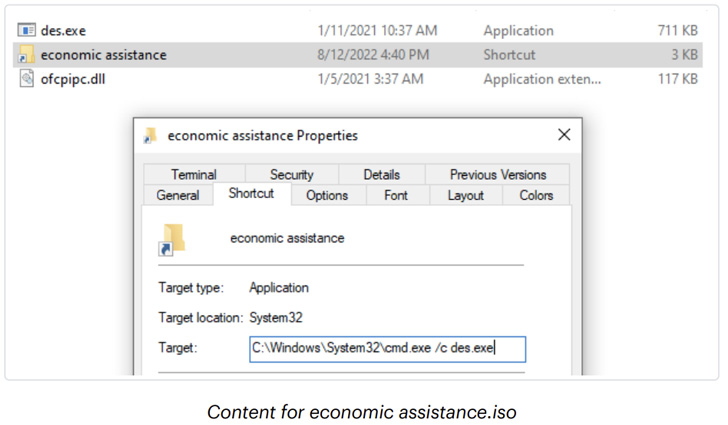
Launching an LNK file contained within the ISO image leads to the execution of the DBoxAgent implant that enables the adversary to remote commandeer the machine and export sensitive data back to the cloud storage service. Dropbox has since disabled the rogue account.
The backdoor further acts as a conduit to drop exploitation tools that would open the door for other attacks and data exfiltration, including activating a multi-stage infection sequence that culminates in the use of an advanced C++ backdoor named KEYPLUG, which was documented by Google’s Mandiant in March 2022.
The development marks the first time APT41 has been observed utilizing Dropbox for C&C purposes, illustrating the growing use by attackers of legitimate software-as-a-service and cloud offerings to host malicious content.
“Winnti remains active and its arsenal keeps growing as one of the most sophisticated groups nowadays,” the cybersecurity firm said. “Sri Lanka’s location in South Asia is strategic for China as it has open access to the Indian Ocean and is close to India.”
