The Chinese state-sponsored threat actor known as Stone Panda has been observed employing a new stealthy infection chain in its attacks aimed at Japanese entities.
Targets include media, diplomatic, governmental and public sector organizations and think-tanks in Japan, according to twin reports published by Kaspersky.
Stone Panda, also called APT10, Bronze Riverside, Cicada, and Potassium, is a cyber espionage group known for its intrusions against organizations identified as strategically significant to China. The threat actor is believed to have been active since at least 2009.
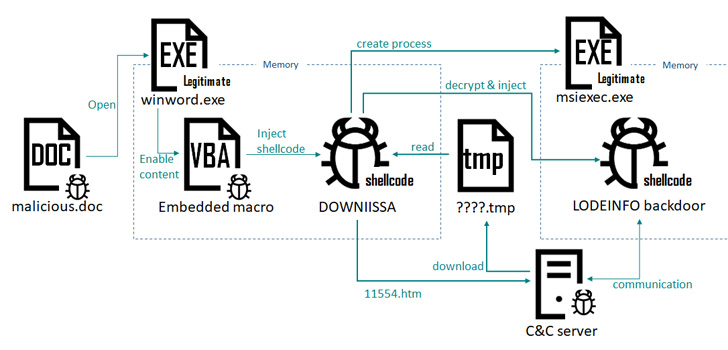
The latest set of attacks, observed between March and June 2022, involve the use of a bogus Microsoft Word file and a self-extracting archive (SFX) file in RAR format propagated via spear-phishing emails, leading to the execution of a backdoor called LODEINFO.
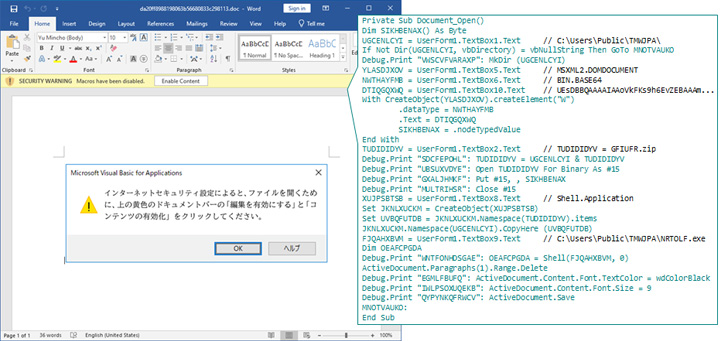
While the maldoc requires users to enable macros to activate the killchain, the June 2022 campaign was found to drop this method in favor of an SFX file that, when executed, displays a harmless decoy Word document to conceal the malicious activities.
The macro, once enabled, drops a ZIP archive containing two files, one of which (“NRTOLF.exe”) is a legitimate executable from the K7Security Suite software that’s subsequently used to load a rogue DLL (“K7SysMn1.dll”) via DLL side-loading.
The abuse of the security application aside, Kaspersky said it also discovered in June 2022 another initial infection method wherein a password-protected Microsoft Word file acted as a conduit to deliver a fileless downloader dubbed DOWNIISSA upon enabling macros.
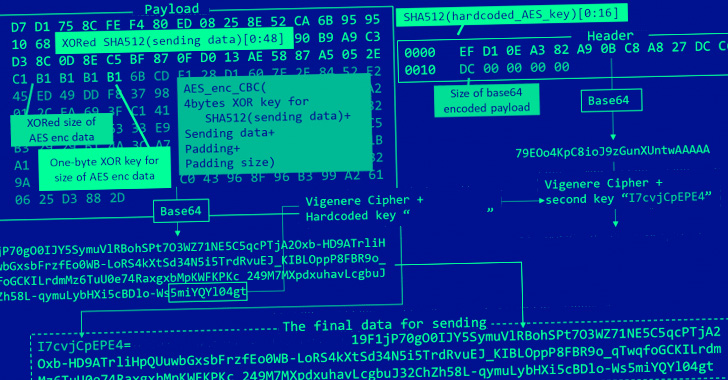
“The embedded macro generates the DOWNIISSA shellcode and injects it in the current process (WINWORD.exe),” the Russian cybersecurity company said.
DOWNIISSA is configured to communicate with a hard-coded remote server, using it to retrieve an encrypted BLOB payload of LODEINFO, a backdoor capable of executing arbitrary shellcode, take screenshots, and exfiltrate files back to the server.

The malware, first seen in 2019, has undergone numerous improvements, with Kaspersky identified six different versions in March, April, June, and September 2022.
The changes include enhanced evasion techniques to fly under the radar, halting execution on machines with the locale “en_US,” revising the list of supported commands, and extending support for Intel 64-bit architecture.
“LODEINFO malware is updated very frequently and continues to actively target Japanese organizations,” the researchers concluded.
“The updated TTPs and improvements in LODEINFO and related malware […] indicate that the attacker is particularly focused on making detection, analysis and investigation harder for security researchers.”