Spotify’s Backstage has been discovered as vulnerable to a severe security flaw that could be exploited to gain remote code execution by leveraging a recently disclosed bug in a third-party module.
The vulnerability (CVSS score: 9.8), at its core, takes advantage of a critical sandbox escape in vm2, a popular JavaScript sandbox library (CVE-2022-36067 aka Sandbreak), that came to light last month.
“An unauthenticated threat actor can execute arbitrary system commands on a Backstage application by exploiting a vm2 sandbox escape in the Scaffolder core plugin,” application security firm Oxeye said in a report shared with The Hacker News.
Backstage is an open source developer portal from Spotify that allows users to create, manage, and explore software components from a unified “front door.” It’s used by many companies like Netflix, DoorDash, Roku, and Expedia, among others.
According to Oxeye, the flaw is rooted in a tool called software templates that can be used to create components within Backstage.
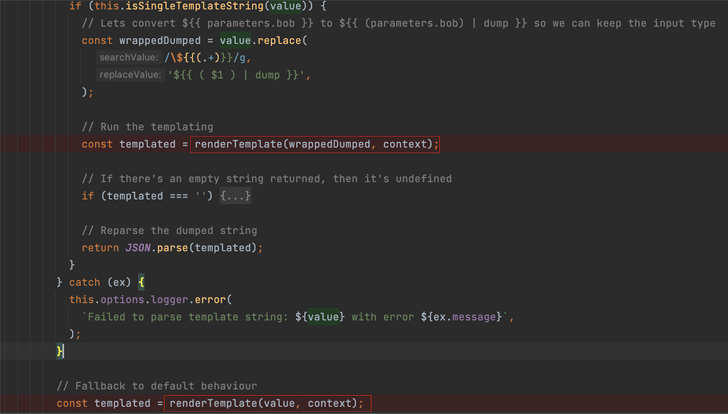 |
| Screenshot shows Backstage calling the renderTemplate function (that calls renderString2) twice in the event of an error. |
While the template engine utilizes vm2 to mitigate the risk associated with running untrusted code, the sandbox escape flaw in the latter made it possible to execute arbitrary system commands outside of the security perimeter.
Oxeye said it was able to identify more than 500 publicly-exposed Backstage instances on the internet, which could then be remotely weaponized by an adversary without requiring any authorization.

Following responsible disclosure on August 18, the issue was addressed by the project maintainers in version 1.5.1 released on August 29, 2022.
“The root of any template-based VM escape is gaining JavaScript execution rights within the template,” the Israeli company noted. “By using ‘logic-less’ template engines such as Mustache, you can avoid introducing server-side template injection vulnerabilities.”
“Separating the logic from the presentation as much as possible can greatly reduce your exposure to the most dangerous template-based attacks,” it further added.
