The Luna Moth campaign has extorted hundreds of thousands of dollars from several victims in the legal and retail sectors.
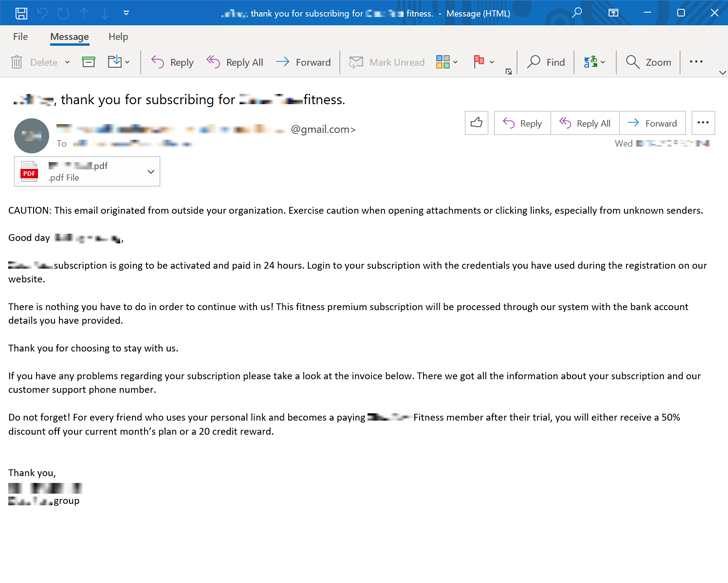
The attacks are notable for employing a technique called callback phishing or telephone-oriented attack delivery (TOAD), wherein the victims are social engineered into making a phone call through phishing emails containing invoices and subscription-themed lures.
Palo Alto Networks Unit 42 said the attacks are the “product of a single highly organized campaign,” adding, “this threat actor has significantly invested in call centers and infrastructure that’s unique to each victim.”
The cybersecurity firm described the activity as a “pervasive multi-month campaign that is actively evolving.”
What’s notable about callback phishing is that the email messages are completely devoid of any malicious attachment or booby-trapped link, allowing them to evade detection and slip past email protection solutions.
These messages typically come with an invoice that includes a phone number that the users can call to cancel the supposed subscription. In reality, however, the victims are routed to an actor-controlled call center and connected to a live agent on the other end, who ends up installing a remote access tool for persistence.
“The attacker will then seek to identify valuable information on the victim’s computer and connected file shares, and they will quietly exfiltrate it to a server they control using a file transfer tool,” Unit 42 researcher Kristopher Russo said.
The campaign may be resource intensive, but is also technically less sophisticated and likely to have a much higher success rate than other phishing attacks.
On top of that, it enables extortion without encryption, permitting malicious actors to plunder sensitive data sans the need to deploy ransomware to lock the files after exfiltration.
The Luna Moth actor, also known as Silent Ransom, has become an expert of sorts when it comes to pulling off such schemes. According to AdvIntel, the cybercrime group is believed to be the mastermind behind the BazarCall attacks last year.
To give these attacks a veneer of legitimacy, the adversaries, instead of dropping a malware like BazarLoader, take advantage of legitimate tools like Zoho Assist to remotely interact with a victim’s computer, abusing the access to deploy other trusted software such as Rclone or WinSCP for harvesting data.
Extortion demands range from two to 78 Bitcoin based on the organization targeted, with the threat actor creating unique cryptocurrency wallets for each payment. The adversary is also said to offer discounts of nearly 25% for prompt payment, although there’s no guarantee that the data is deleted.
“The threat actors behind this campaign have taken great pains to avoid all non-essential tools and malware, to minimize the potential for detection,” Russo said. “Since there are very few early indicators that a victim is under attack, employee cybersecurity awareness training is the first line of defense.”
