The cyber espionage group known as Bahamut has been attributed as behind a highly targeted campaign that infects users of Android devices with malicious apps designed to extract sensitive information.
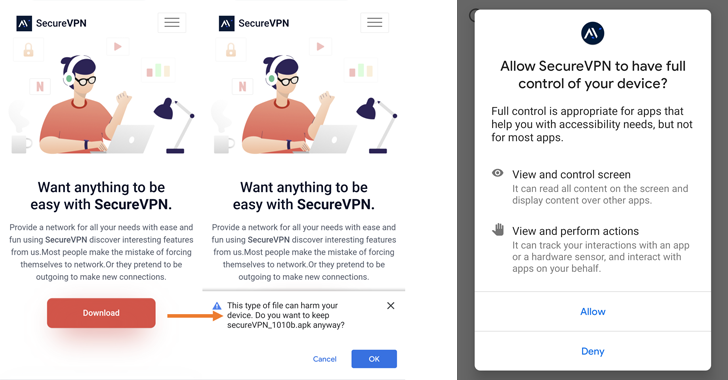
The activity, which has been active since January 2022, entails distributing rogue VPN apps through a fake SecureVPN website set up for this purpose, Slovak cybersecurity firm ESET said in a new report shared with The Hacker News.
At least eight different variants of the spyware apps have been discovered to date, with them being trojanized versions of legitimate VPN apps like SoftVPN and OpenVPN.
The tampered apps and their updates are pushed to users through the fraudulent website. It’s also suspected that the targets are carefully selected, since launching the app requires the victim to enter an activation key to enable the features.
This implies the use of an undetermined distribution vector, although past evidence shows that it could take the form of spear-phishing emails, SMS messages, or direct messages on social media apps.
The activation key mechanism is also designed to communicate with an actor-controlled server, effectively preventing the malware from being accidentally triggered right after launch on a non-targeted user device.
Bahamut was unmasked in 2017 by Bellingcat as a hack-for-hire operation targeting government officials, human rights groups, and other high-profile entities in South Asia and the Middle East with malicious Android and iOS apps to spy on its victims.
“Perhaps the most distinctive aspect of Bahamut’s tradecraft that BlackBerry discovered is the group’s use of original, painstakingly crafted websites, applications and personas,” BlackBerry noted in October 2020.
Earlier this year, Cyble detailed two sets of phishing attacks orchestrated by the group to push counterfeit Android apps masquerading as chat applications.
The latest wave follows a similar trajectory, tricking users into installing seemingly innocuous VPN apps that can exfiltrate a wide swathe of information, including files, contact lists, SMSes, phone call recordings, locations, and messages from WhatsApp, Facebook Messenger, Signal, Viber, Telegram, and WeChat.
“The data exfiltration is done via the keylogging functionality of the malware, which misuses accessibility services,” ESET researcher Lukáš Štefanko said.
In a sign that the campaign is well maintained, the threat actor initially packaged the malicious code within the SoftVPN application, before moving to OpenVPN, a shift explained by the fact that the actual SoftVPN app stopped functioning and it was no longer possible to establish a VPN connection.
“The mobile campaign operated by the Bahamut APT group is still active; it uses the same method of distributing its Android spyware apps via websites that impersonate or masquerade as legitimate services, as has been seen in the past,” Štefanko added.