The Lazarus Group threat actor has been observed leveraging fake cryptocurrency apps as a lure to deliver a previously undocumented version of the AppleJeus malware, according to new findings from Volexity.
“This activity notably involves a campaign likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by way of malicious Microsoft Office documents,” researchers Callum Roxan, Paul Rascagneres, and Robert Jan Mora said.
The North Korean government is known to adopt a three-pronged approach by employing malicious cyber activity that’s orchestrated to collect intelligence, conduct attacks, and generate illicit revenue for the sanctions hit nation. The threats are collectively tracked under the name Lazarus Group (aka Hidden Cobra or Zinc).

“North Korea has conducted cyber theft against financial institutions and cryptocurrency exchanges worldwide, potentially stealing hundreds of millions of dollars, probably to fund government priorities, such as its nuclear and missile programs,” per the 2021 Annual Threat Assessment released by U.S. intelligence agencies.
Earlier this April, the Cybersecurity and Infrastructure Security Agency (CISA) warned of an activity cluster dubbed TraderTraitor that targets cryptocurrency exchanges and trading companies through trojanized crypto apps for Windows and macOS.
While the TraderTraitor attacks culminate in the deployment of the Manuscrypt remote access trojan, the new activity makes use of a supposed crypto trading website named BloxHolder, a copycat of the legitimate HaasOnline platform, to deliver AppleJeus via an installer file.
AppleJeus, first documented by Kaspersky in 2018, is designed to harvest information about the infected system (i.e., MAC address, computer name, and operating system version) and download shellcode from a command-and-control (C2) server.
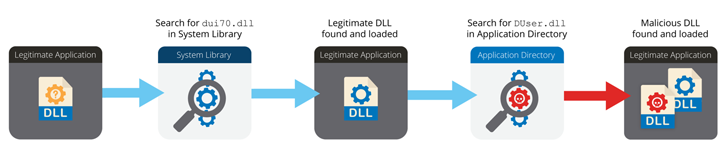
The attack chain is said to have undergone a slight deviation in October 2022, with the adversary shifting from MSI installer files to a booby-trapped Microsoft Excel document that uses macros to download a remotely hosted payload, a PNG image, from OpenDrive.
The idea behind the switch is likely to reduce static detection by security products, Volexy said, adding it couldn’t obtain the image file (“Background.png”) from the OpenDrive link but noted it embeds three files, including an encoded payload that’s subsequently extracted and launched on the compromised host.
“The Lazarus Group continues its effort to target cryptocurrency users, despite ongoing attention to their campaigns and tactics,” the researchers concluded.
