An Iranian advanced persistent threat (APT) actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong.
The wiper, referred to as Fantasy by ESET, is believed to have been delivered via a supply-chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.
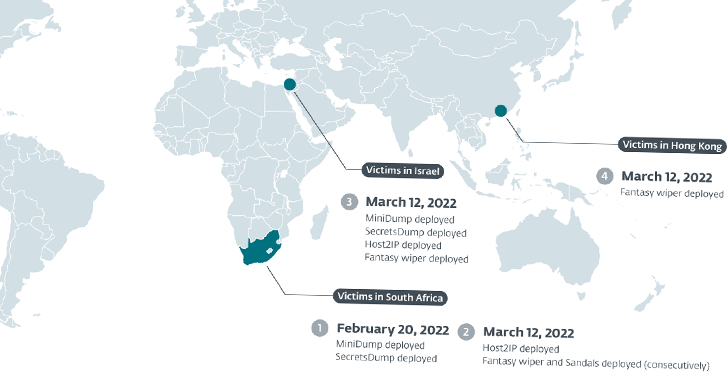
Victims include HR firms, IT consulting companies, and a diamond wholesaler in Israel; a South African entity working in the diamond industry; and a jeweller based in Hong Kong.
“The Fantasy wiper is built on the foundations of the previously reported Apostle wiper but does not attempt to masquerade as ransomware, as Apostle originally did, ESET researcher Adam Burgher disclosed in a Wednesday analysis. “Instead, it goes right to work wiping data.”
Apostle was first documented by SentinelOne in May 2021 as a wiper-turned-ransomware that was deployed in destructive attacks against Israeli targets.

Agrius, the Iran-aligned group behind the intrusions, has been active since at least December 2020 and leverages known security flaws in internet-facing applications to drop web shells that are, in turn, used to facilitate reconnaissance, lateral movement, and the delivery of final-stage payloads.
The Slovak cybersecurity company said the first attack was detected on February 20, 2022, when the actor deployed credential harvesting tools in the IT network of the South African organization.
Agrius subsequently initiated the wiping attack via Fantasy on March 12, 2022, before striking other companies in Israel and Hong Kong on the same date.
Fantasy is executed by means of another tool called Sandals, a 32-bit Windows executable written in C#/.NET. It’s said to be deployed on the compromised host through a supply-chain attack using the Israeli developer’s software update mechanism.
This is substantiated by ESET’s assessment that all victims are customers of the affected software developer and that the wiper binary follows a naming convention (“fantasy45.exe” and “fantasy35.exe”) similar to that of its legitimate counterpart.
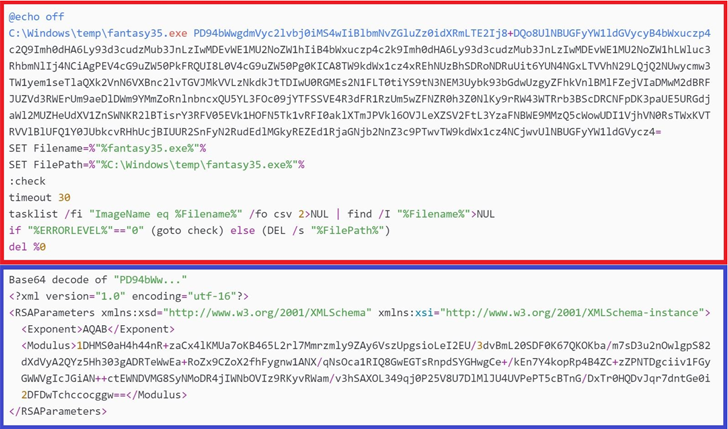
The wiper, for its part, works by recursively retrieving the directory listing for each drive, overwriting every file in those directories with garbage data, assigning a future timestamp to the files, and then deleting them.
“This is presumably done to make recovery and forensic analysis more difficult,” Burgher explained.
In a further attempt to erase all traces of the activity, Fantasy clears all Windows event logs, recursively purges all files in the system drive, overwrites the system’s Master Boot Record, self-deletes itself, and finally reboots the machine.
The campaign, which lasted no more than three hours, was ultimately unsuccessful, with ESET stating that it was able to block the wiper’s execution. The developer of the software has since pushed out clean updates to plug the attacks.
The name of the Israeli company that fell victim to the supply-chain attack was not disclosed by ESET, but evidence points to it being Rubinstein Software, which markets an enterprise resource planning (ERP) solution called Fantasy that’s used for jewelry stock management.
“Since its discovery in 2021, Agrius has been solely focused on destructive operations,” Burgher concluded.
“To that end, Agrius operators probably executed a supply-chain attack by targeting an Israeli software company’s software updating mechanisms to deploy Fantasy, its newest wiper, to victims in Israel, Hong Kong, and South Africa.”
Agrius is far from the first threat group linked to Iran that has been spotted deploying destructive wiper malware.
The APT33 hacking group (aka Elfin, Holmium, or Refined Kitten), which is suspected of operating at the behest of the Iranian government, is said to have been behind multiple attacks that used the Shamoon wiper against targets located in the Middle East.
Data-wiping malware codenamed ZeroCleare has also been employed by Iran-backed threat actors tracked as APT34 (aka Oilrig or Helix Kitten) in attacks directed against organizations from the energy and industrial sector in the Middle East.