An ongoing analysis of the KmsdBot botnet has raised the possibility that it’s a DDoS-for-hire service offered to other threat actors.
This is based on the different industries and geographies that were attacked, web infrastructure company Akamai said. Among the notable targets included FiveM and RedM, which are game modifications for Grand Theft Auto V and Red Dead Redemption 2, as well as luxury brands and security firms.
KmsdBot is a Go-based malware that leverages SSH to infect systems and carry out activities like cryptocurrency mining and launch commands using TCP and UDP to mount distributed denial-of-service (DDoS) attacks.

However, a lack of an error-checking mechanism in the malware source code caused the malware operators to inadvertently crash their own botnet last month.
“Based on observed IPs and domains, the majority of the victims are located in Asia, North America, and Europe,” Akamai researchers Larry W. Cashdollar and Allen West said. “The presence of these commands tracks with previous observations of targeted gaming servers and offers a glimpse into the customers of this botnet for hire.”
Akamai, which examined the attack traffic, identified 18 different commands that KmsdBot accepts from a remote server, one of which, dubbed “bigdata,” caters to sending junk packets containing large amounts of data to a target in an attempt to exhaust its bandwidth.
Also included are commands such as “fivem” and “redm” that are designed to target video game mod servers, alongside a “scan” instruction that “appears to target specific paths within the target environment.”
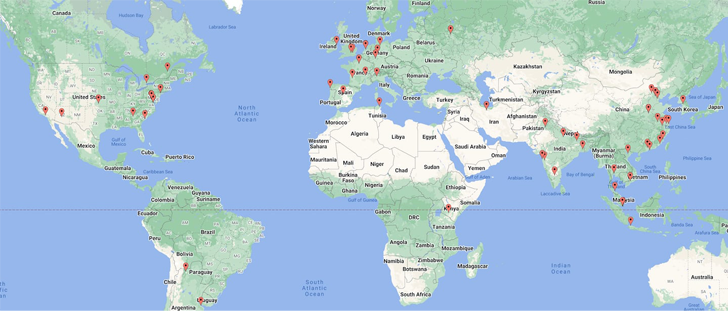
Charting the infection attempts of the botnet signals minimal activity in the Russian territory and neighboring regions, potentially offering a clue as to its origins.
A further breakdown of the attack commands observed over a 30-day time period shows “bigdata” leading with a frequency of more than 70. Calls to “fivem” have occurred 45 times, while “redm” has seen less than 10 calls.
“This tells us that although gaming servers are a specific target offered, it may not be the only industry that is being hit with these attacks,” the researchers said. “Support for multiple types of servers increases the overall usability of this botnet and appears to be effective in driving in customers.”
The findings come a week after Microsoft detailed a cross-platform botnet known as MCCrash that comes with capabilities to carry out DDoS attacks against private Minecraft servers.