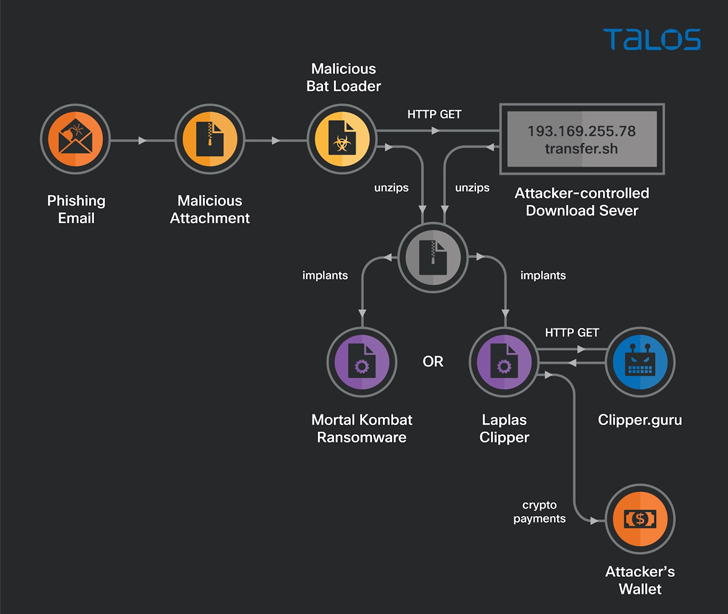
A new financially motivated campaign that commenced in December 2022 has seen the unidentified threat actor behind it deploying a novel ransomware strain dubbed MortalKombat and a clipper malware known as Laplas.
Cisco Talos said it “observed the actor scanning the internet for victim machines with an exposed remote desktop protocol (RDP) port 3389.”
The attacks, per the cybersecurity company, primarily focuses on individuals, small businesses, and large organizations located in the U.S., and to a lesser extent in the U.K., Turkey, and the Philippines.
The starting point that kicks off the multi-stage attack chain is a phishing email bearing a malicious ZIP file that’s used as a pathway to deliver either the clipper or the ransomware.
In addition to using cryptocurrency-themed email lures impersonating CoinPayments, the threat actor is also known to erase infection markers in an attempt to cover its tracks.
MortalKombat, first detected in January 2023, is capable of encrypting system, application, backup, and virtual machine files in the compromised system. It further corrupts Windows Explorer, disables the Run command window, and removes applications and folders from Windows startup.
A source code analysis of the ransomware reveals that it’s part of the Xorist family of ransomware, Cisco Talos researcher Chetan Raghuprasad said.
The Laplas clipper is a Golang variant of malware that came to light in November 2022. It’s designed to monitor the clipboard for any cryptocurrency wallet address and substitute it with an actor-controlled wallet to carry out fraudulent transactions.
“The clipper reads the victim machine’s clipboard contents and executes a function to perform regular expression pattern matching to detect the cryptocurrency wallet address,” Raghuprasad explained.
“When a cryptocurrency wallet address is identified, the clipper sends the wallet address back to the clipper bot. In response, the clipper receives an attacker-controlled wallet address similar to the victim’s and overwrites the original cryptocurrency wallet address in the clipboard.”
