Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency.
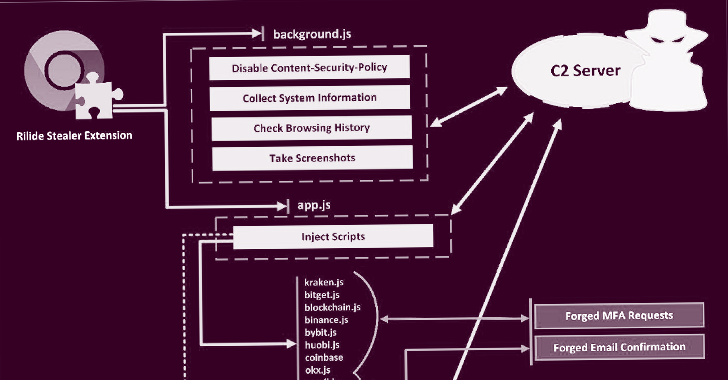
“Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring
browsing history, taking screenshots, and injecting malicious scripts to withdraw funds from various cryptocurrency exchanges,” Trustwave SpiderLabs Research said in a report shared with The Hacker News.
What’s more, the stealer malware can display forged dialogs to deceive users into entering a two-factor authentication code to withdraw digital assets.
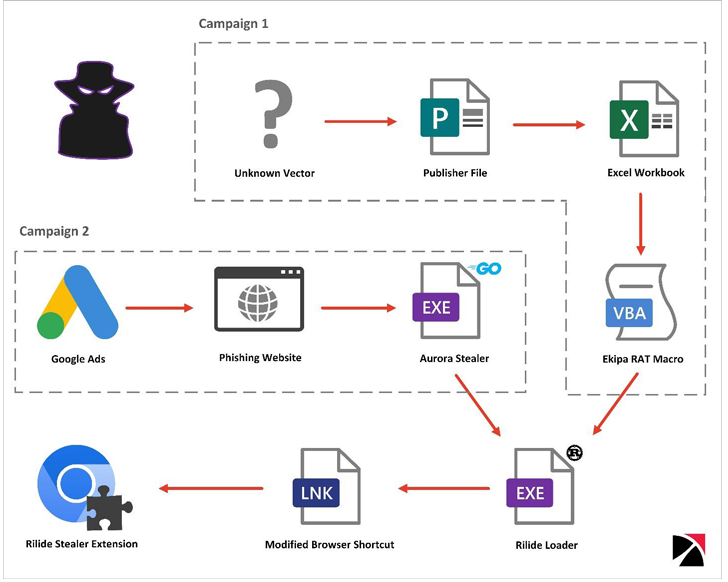
Trustwave said it identified two different campaigns involving Ekipa RAT and Aurora Stealer that led to the installation of the malicious browser extension.
While Ekipa RAT is distributed via booby-trapped Microsoft Publisher files, rogue Google Ads act as the delivery vector for Aurora Stealer – a technique that’s become increasingly common in recent months.
Both the attack chains facilitate the execution of a Rust-based loader that, in turn, modifies the browser’s LNK shortcut file and makes use of the “–load-extension” command line switch to launch the add-on.
The exact origins of Rilide is unknown, but Trustwave said it was able to find an underground forum post made in March 2022 by a threat actor advertising the sale of a botnet with similar functionalities.
A portion of the malware’s source code has since found its way to the forums following what appears to be an unresolved payment dispute.
Become an Incident Response Pro!
Unlock the secrets to bulletproof incident response – Master the 6-Phase process with Asaf Perlman, Cynet’s IR Leader!
Don’t Miss Out – Save Your Seat!
One notable feature implemented in the leaked source code is the ability to swap cryptocurrency wallet addresses in the clipboard with an actor-controlled address hard-coded in the sample.
Furthermore, a command-and-control (C2) address specified in the Rilide code has made it possible to identify various GitHub repositories belonging to a user named gulantin that contain loaders for the extension.
“The Rilide stealer is a prime example of the increasing sophistication of malicious browser extensions and the dangers they pose,” Trustwave concluded.
“While the upcoming enforcement of manifest v3 may make it more challenging for threat actors to operate, it is unlikely to solve the issue entirely as most of the functionalities leveraged by Rilide will still be available.”