Today, businesses face a variety of security challenges like cyber attacks, compliance requirements, and endpoint security administration. The threat landscape constantly evolves, and it can be overwhelming for businesses to keep up with the latest security trends. Security teams use processes and security solutions to curb these challenges. These solutions include firewalls, antiviruses, data loss prevention services, and XDRs (Extended Detection and Response).
Wazuh is a free and open source security platform that unifies XDR and SIEM (System Information and Event Management) capabilities. It comprises a universal security agent for event data collection from various sources and the central components for event analysis, correlation, and alerting. The central components include the Wazuh server, dashboard, and indexer. Wazuh offers a suite of modules capable of providing extended threat detection and response for on-premises and cloud workloads.
In this article, we emphasize the capabilities of Wazuh that are beneficial to your organization’s security needs.
Threat intelligence
Wazuh includes the MITRE ATT&CK module with threat detection rules out-of-the-box. The MITRE ATT&CK module provides details that allow threat hunters to recognize adversary tactics, techniques, and procedures (TTPs). These include details such as the threat groups, software, and mitigation measures. You can use this information to narrow down threats or compromised endpoints in your environment. Wazuh threat detection rules are mapped against their corresponding MITRE ATT&CK IDs.
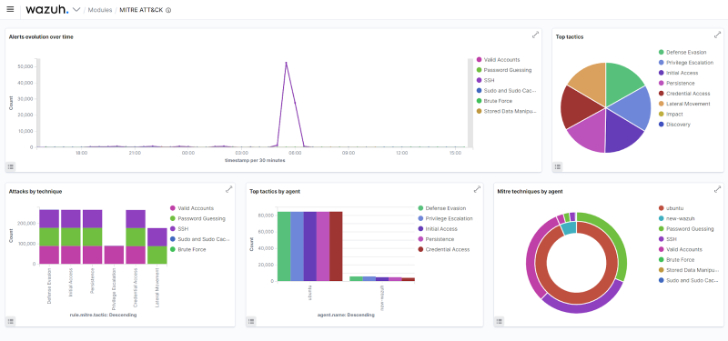 |
| Fig 1: Wazuh MITRE ATT&CK dashboard |
Wazuh integrates seamlessly with third-party threat intelligence solutions like VirusTotal, MISP, URLHaus, and YARA. These integrations enable the checking of file hashes, IP addresses, and URLs against recognized malicious indicators of compromise (IOCs). Wazuh integration with these solutions improves your business’ overall security posture by providing additional insights on potential threats, malicious activities, and IOCs.
A Vulnerability is a security weakness or flaw that can be exploited by threats to perform malicious activities in a computer system. Wazuh offers the Vulnerability Detector module to help businesses identify and prioritize vulnerabilities in their environments. This module uses data from multiple feeds such as Canonical, Microsoft, the National Vulnerability Database (NVD), and more to provide real-time information about vulnerabilities.
Threat detection and response
Wazuh uses its modules, decoders, ruleset, and integration with third-party solutions to detect and protect your digital assets from threats. These threats include malware, web, network attacks, and more.
The Wazuh File Integrity Monitoring module monitors directories and reports file addition, deletion, and modifications. It is used to audit sensitive files but can be combined with other integrations to detect malware. The rootcheck module is used to detect rootkit behaviors like hidden files, ports, and unusual processes. The Wazuh active response module provides automated response actions such as quarantining infected systems, blocking network traffic, or terminating the ransomware processes. The combination of these modules allows for a quick response to mitigate the impact of cyberattacks.
The image below illustrates the combination of the FIM module, VirusTotal integration, and the active response module in detecting and responding to malware downloaded on a monitored endpoint.
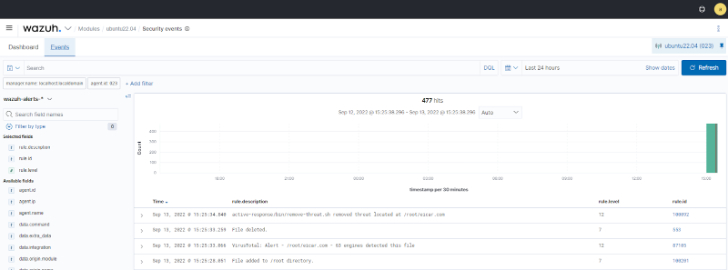 |
| Fig 2: Malicious file detected and deleted from a monitored endpoint |
Audit and regulatory compliance
Security auditing and compliance are two important concepts for any business that aims to protect itself against cyber attacks. Security auditing is the systematic process of evaluating an organization’s information systems, practices, and procedures to identify vulnerabilities, assess risks, and ensure that security controls function as intended. Regulatory compliance refers to the process of certifying that an organization adheres to a set of established standards, regulations, or laws related to information security.
Wazuh helps businesses pass security audits and meet regulatory compliance requirements. Compliance standards offer a set of guidelines and optimal procedures to guarantee the safety of an organization’s systems, network, and data. Adhering to these standards helps lower the likelihood of a security breach. Wazuh has various modules that help meet compliance standards like PCI DSS, GDPR, NIST, etc. The post Using the Wazuh SIEM and XDR platform to meet PCI DSS compliance shows how Wazuh plays an important role in maintaining PCI compliance for your organization. The image below shows a Wazuh NIST dashboard.
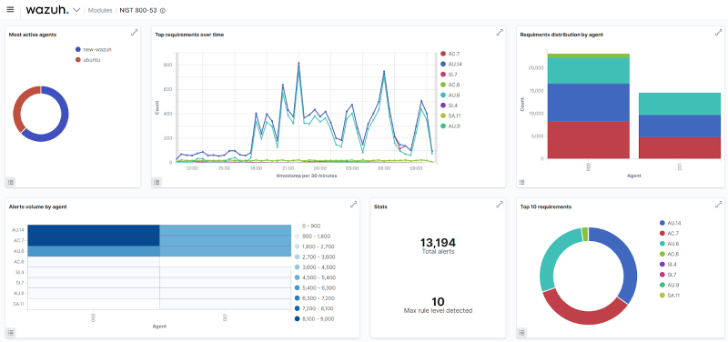 |
| Fig 3: The Wazuh NIST dashboard |
Cloud security
Cloud platforms provide services that manage computing, storage, and networking operations through the Internet. Businesses are widely adopting these cloud platforms because of their easy access to resources, flexibility, and high scalability. As more organizations leverage the use of the cloud, maintaining the security of their digital assets remains critical.
Wazuh is a unified XDR and SIEM platform that provides visibility and security monitoring for cloud environments. It monitors and protects cloud services running on Amazon Web Services, Microsoft Azure, and Google Cloud Platform. It achieves this by collecting and analyzing security event data from various cloud components. Such data allows Wazuh to perform vulnerability detection, cloud compliance checks, security monitoring, and automated responses to detected threats.
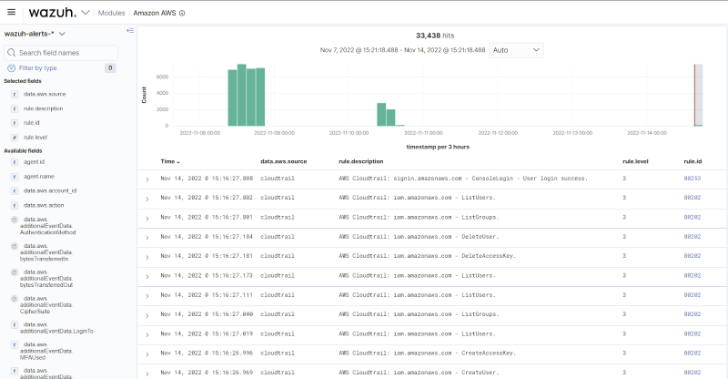 |
| Fig 4: Wazuh monitoring the AWS CloudTrail service |
Endpoint hardening
The Wazuh SCA module performs configuration assessments on systems and applications, ensuring the host is secure and the vulnerability surface is reduced. Wazuh uses policy files to scan endpoints for misconfigurations and vulnerabilities. These policy files are included out-of-the-box and based on the Center for Internet Security (CIS) benchmark. The SCA scan results provide insight into the vulnerabilities present on a monitored endpoint. These vulnerabilities range from configuration flaws to installed vulnerable versions of the applications and services. Failed security checks are displayed alongside their remediation, giving system administrators a quick resolution pathway.
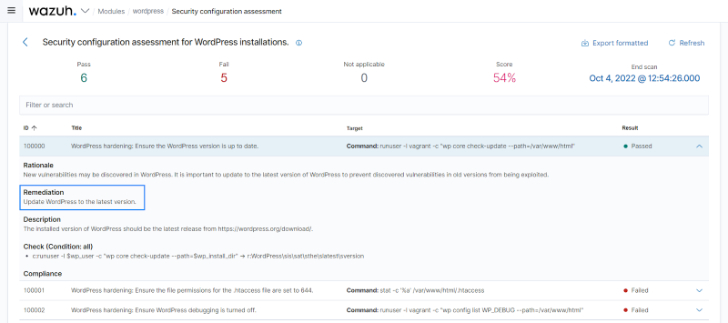 |
| Fig 5: Failed SCA check and remediation for a WordPress installation |
Open source
Wazuh has a fast-growing community where users, developers, and contributors can ask questions about the platform and share collaborative ideas. The Wazuh community provides users with free support, resources, and documentation.
Wazuh, as an open source security platform, provides easy flexibility and customization. Users can modify the source code to suit their specific needs or add new features and capabilities. The Wazuh source code is publicly available on the Wazuh GitHub repository for users that may wish to perform verification checks or contributions.
Conclusion
Wazuh is a free and open source platform with robust XDR and SIEM capabilities. With capabilities such as log data analysis, file integrity monitoring, intrusion detection, and automated response, Wazuh gives businesses the ability to quickly and effectively respond to security incidents.
