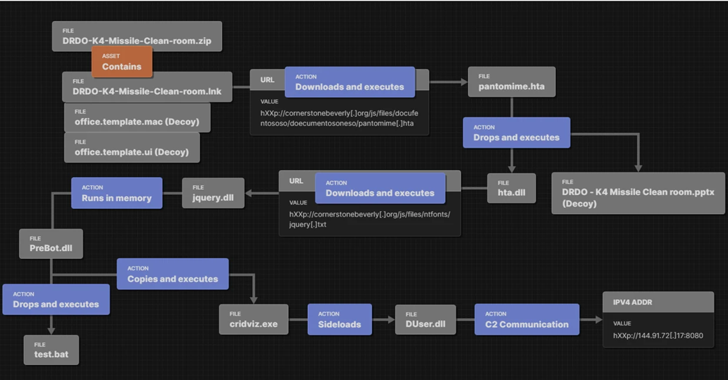
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research organization as part of an ongoing phishing campaign.
This involves using a ZIP archive lure pertaining to India’s Defence Research and Development Organization (DRDO) to deliver a malicious payload capable of harvesting sensitive information, Fortinet FortiGuard Labs said in a new report.
The cyber espionage group, with activity dating back to at least 2019, targets entities that align with Pakistan government interests. It’s believed to share overlaps with another Pakistani hacking crew called Transparent Tribe.

SideCopy’s use of DRDO-related decoys for malware distribution was previously flagged by Cyble and Chinese cybersecurity firm QiAnXin in March 2023, and again by Team Cymru last month.
Interestingly, the same attack chains have been observed to load and execute Action RAT as well as an open source remote access trojan known as AllaKore RAT.
The latest infection sequence documented by Fortinet is no different, leading to the deployment of an unspecified strain of RAT that’s capable of communicating with a remote server and launching additional payloads.
The development is an indication that SideCopy has continued to carry out spear-phishing email attacks that use Indian government and defense forces-related social engineering lures to drop a wide range of malware.
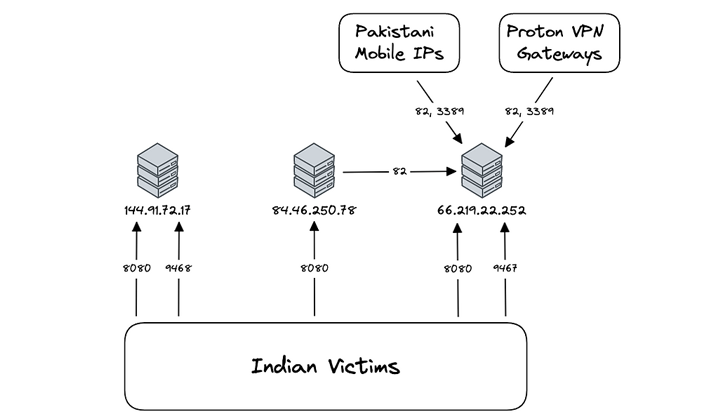 |
| Source: Team Cymru |
Further analysis of the Action RAT command-and-control (C2) infrastructure by Team Cymru has identified outbound connections from one of the C2 server IP addresses to another address 66.219.22[.]252, which is geolocated in Pakistan.
The cybersecurity company also said it observed “communications sourced from 17 distinct IPs assigned to Pakistani mobile providers and four Proton VPN nodes,” noting inbound connections to the IP address from IP addresses assigned to Indian ISPs.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
In all, as many as 18 distinct victims in India have been detected as connecting to C2 servers associated with Action RAT and 236 unique victims, again located in India, connecting to C2 servers associated with AllaKore RAT.
The latest findings lend credence to SideCopy’s Pakistan links, not to mention underscore the fact that the campaign has been successful in targeting Indian users.
“The Action RAT infrastructure, connected to SideCopy, is managed by users accessing the Internet from Pakistan,” Team Cymru said. “Victim activity predated the public reporting of this campaign, in some cases by several months.”