The threat actors behind the CopperStealer malware resurfaced with two new campaigns in March and April 2023 that are designed to deliver two novel payloads dubbed CopperStealth and CopperPhish.
Trend Micro is tracking the financially motivated group under the name Water Orthrus. The adversary is also assessed to be behind another campaign known as Scranos, which was detailed by Bitdefender in 2019.
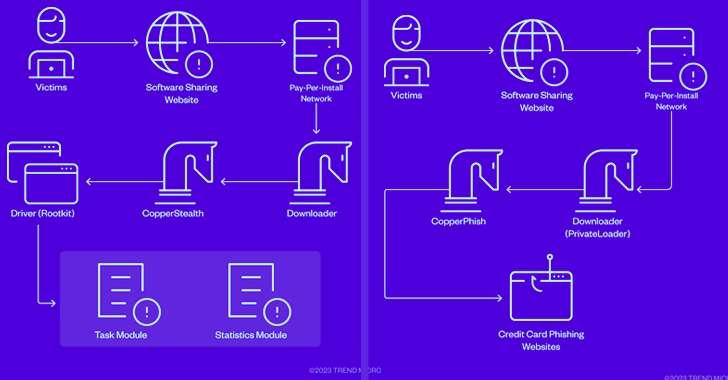
Active since at least 2021, Water Orthrus has a track record of leveraging pay-per-install (PPI) networks to redirect victims landing on cracked software download sites to drop an information stealer codenamed CopperStealer.
Another campaign spotted in August 2022 entailed the use of CopperStealer to distribute Chromium-based web browser extensions that are capable of performing unauthorized transactions and transferring cryptocurrency from victims’ wallets to ones under attackers’ control.

The latest attack sequences documented by Trend Micro don’t mark much of a deviation, propagating CopperStealth by packaging it as installers for free tools on Chinese software-sharing websites.
“CopperStealth’s infection chain involves dropping and loading a rootkit, which later injects its payload into explorer.exe and another system process,” security researchers Jaromir Horejsi and Joseph C Chen said in a technical report.
“These payloads are responsible for downloading and running additional tasks. The rootkit also blocks access to blocklisted registry keys and prevents certain executables and drivers from running.”
The driver denylist contains byte sequences pertaining to Chinese security software companies like Huorong, Kingsoft, and Qihoo 360.
CopperStealth also incorporates a task module that enables it to call out to a remote server and retrieve the command to be executed on the infected machine, equipping the malware to drop more payloads.
File Sharing Websites Act as Conduit for CopperPhish Phishing Kit
The CopperPhish campaign, detected worldwide in April 2023, takes advantage of an analogous process to deploy the malware via PPI networks behind free anonymous file-sharing websites.
“Visitors will be redirected to a download page designed by the PPI network after clicking on its advertisements, which pretended to be a download link,” the researchers said. “The downloaded file is PrivateLoader, which downloads and runs many different malware.”
The downloader service, which is also offered on a PPI basis, is then used to retrieve and launch CopperPhish, a phishing kit that’s responsible for harvesting credit card information.
It achieves this by “starting a rundll32 process and injecting a simple program with a browser window (written in Visual Basic) in it,” which loads a phishing page urging victims to scan a QR code in order to verify their identity and enter a confirmation code to “restore your device’s network.”
“The window has no controls that can be used to minimize or close it,” the researchers explained. “The victim could close the browser’s process in Task Manager or Process Explorer, but they would also need to terminate the main payload process, otherwise the browser process will happen again due to the persistence thread.”
Once the sensitive details are entered in the page, the CopperPhish malware displays the message “the identity verification has passed” alongside a confirmation code that the victim can enter on the aforementioned screen.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
Providing the correct confirmation code also causes the malware to uninstall itself and delete all the dropped phishing files from the machine.
“The credential verification and confirmation code are two useful features that make this phishing kit more successful, as the victim cannot simply close the window or enter fake information just to get rid of the window,” the researchers said.
The attribution to Water Orthrus is based on the fact that both CopperStealth and CopperPhish share similar source code characteristics as that of CopperStealer, raising the possibility that all three strains may have been developed by the same author.
The disparate objectives of the campaigns represent the evolution of the threat actor’s tactics, indicating an attempt to add new capabilities to its arsenal and expand its financial horizons.
The findings come as malicious Google ads are being used to entice users into downloading fake installers for AI tools like Midjourney and OpenAI’s ChatGPT that ultimately drop stealers such as Vidar and RedLine.
They also follow the discovery of a new traffic-monetizing service called TrafficStealer that leverages misconfigurations containers to redirect traffic to websites and generate fake ad clicks as part of an illicit money-making scheme.