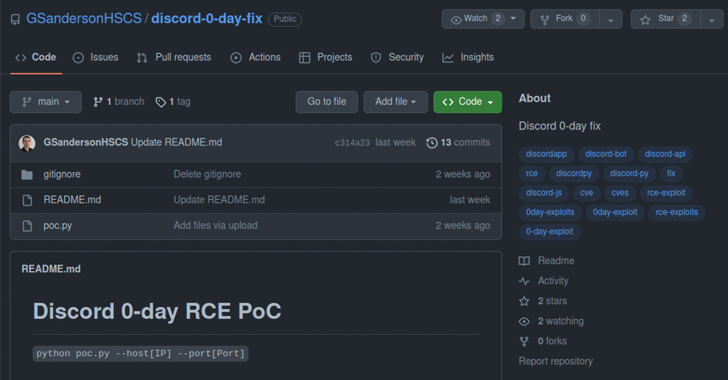
At least half of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity company have been observed pushing malicious repositories on the code hosting service.
All seven repositories, which are still available as of writing, claim to be a proof-of-concept (PoC) exploit for purported zero-day flaws in Discord, Google Chrome, and Microsoft Exchange.
VulnCheck, which discovered the activity, said, “the individuals creating these repositories have put significant effort into making them look legitimate by creating a network of accounts and Twitter profiles, pretending to be part of a non-existent company called High Sierra Cyber Security.”

The cybersecurity firm said it first came across the rogue repositories in early May when they were observed pushing similar PoC exploits for zero-day bugs in Signal and WhatsApp. The two repositories have since been taken down.
Besides sharing some of the purported findings on Twitter in an attempt to build legitimacy, the network of accounts even uses headshots of actual security researchers from companies like Rapid7, suggesting that the threat actors put significant effort into crafting the campaign.
The PoC is a Python script that’s designed to download a malicious binary and execute it on the victim’s operating system, be it Windows or Linux.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Join the Session
“The attacker has made a lot of effort to create all these fake personas, only to deliver very obvious malware,” VulnCheck researcher Jacob Baines said. “It’s unclear if they have been successful, but given that they’ve continued to pursue this avenue of attacks, it seems they believe they will be successful.”
It’s currently not known if this is the work of an amateur actor or an advanced persistent threat (APT). But security researchers have previously come under the radar of North Korean nation-state groups, as revealed by Google in January 2021.
If anything, the findings show the need for exercising caution when it comes to downloading code from open source repositories. It’s also essential that users scrutinize the code prior to execution to ensure they don’t pose any security risks.