Multiple security flaws have been disclosed in Apache OpenMeetings, a web conferencing solution, that could be potentially exploited by malicious actors to seize control of admin accounts and run malicious code on susceptible servers.
“Attackers can bring the application into an unexpected state, which allows them to take over any user account, including the admin account,” Sonar vulnerability researcher Stefan Schiller said in a report shared with The Hacker News.
“The acquired admin privileges can further be leveraged to exploit another vulnerability allowing attackers to execute arbitrary code on the Apache OpenMeetings server.”
Following responsible disclosure on March 20, 2023, the vulnerabilities were addressed with the release of Openmeetings version 7.1.0 that was released on May 9, 2023. The list of three flaws is as follows –
- CVE-2023-28936 (CVSS score: 5.3) – Insufficient check of invitation hash
- CVE-2023-29032 (CVSS score: 8.1) – An authentication bypass that leads to unrestricted access via invitation hash
- CVE-2023-29246 (CVSS score: 7.2) – A NULL byte (%00) injection that allows an attacker with admin privileges to gain code execution
Meeting invites created using OpenMeetings come are not only bound to a specific room and a user but also come with a unique hash that’s used by the application to retrieve details associated with the invitation.
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
Join Today
The first two flaws, in a nutshell, have to do with a weak hash comparison between the user-supplied hash and what’s present in the database and a quirk that allows for the creation of a room invitation without a room assigned to it, leading to a scenario where an invitation exists with no room attached to it.
A threat actor could exploit these shortcomings to create an event and join the corresponding room, and follow it up by deleting the event, at which point an invitation is created for the admin user to the non-existing room. In the next step, the weak hash comparison bug could be leveraged to enumerate the sent invitation and redeem it by providing a wildcard hash input.
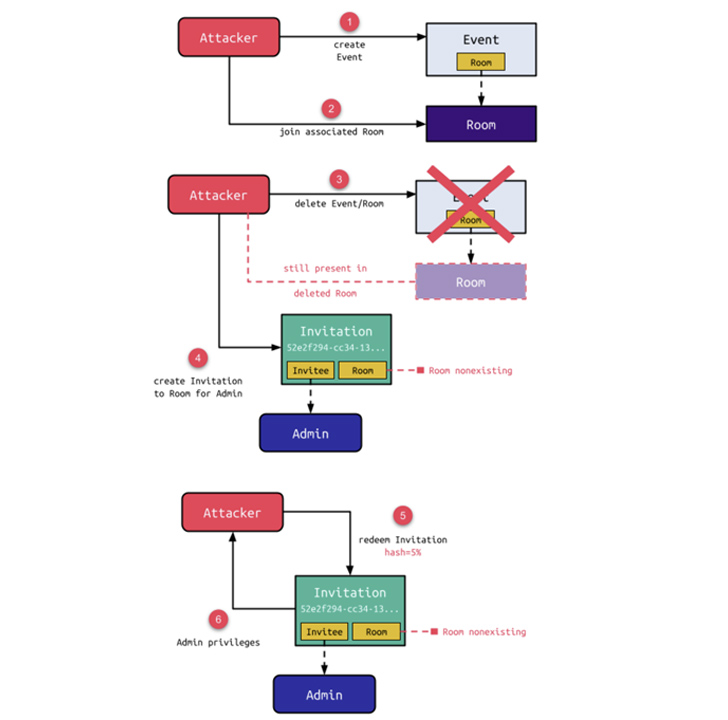
“Although the room is also deleted when its associated event is deleted, the presence of the attacker in the room makes this a zombie room,” Schiller explained. “Although an error is raised when redeeming the hash for such an invitation, a valid web session for the invitee with full permissions of this user is created.”
In other words, the zombie room could allow the attacker to acquire admin privileges and make modifications to the OpenMeetings instance, including adding and removing users and groups, changing room settings, and terminating sessions of connected users.
Sonar said it also identified a third vulnerability that’s rooted in a feature that enables an administrator to configure the path for executables related to ImageMagick, an open-source software used to edit and process images. This allows an attacker with admin privileges to gain code execution by changing the ImageMagic path to “/bin/sh%00x” and triggering arbitrary shell commands.
“When now uploading a fake image containing a valid image header followed by arbitrary shell commands, the conversion spawns /bin/sh with the first argument being the fake image, effectively executing every command in it,” Schiller said.
“In combination with the account takeover, this vulnerability allows a self-registered attacker to gain remote code execution on the underlying server.”
