Validate security continuously across your full stack with Pen Testing as a Service.
In today’s modern security operations center (SOC), it’s a battle between the defenders and the cybercriminals. Both are using tools and expertise – however, the cybercriminals have the element of surprise on their side, and a host of tactics, techniques, and procedures (TTPs) that have evolved. These external threat actors have now been further emboldened in the era of AI with open-source tools like ChatGPT.
With the potential of an attack leading to a breach within minutes, CISOs now are looking to prepare all systems and assets for cyber resilience and rapid response when needed.
With tools and capabilities to validate security continuously – including penetration testing as a service – DevSecOps teams can remediate critical vulnerabilities fast due to the easy access to tactical support to the teams that need it the most. This gives the SOC and DevOps teams tools to that remove false positives, validate findings, and streamline remediation and incident response. This effective investment provides a game-point advantage that gives back time to the SOC by reducing events, incidents, and breaches that require the SOC to detect and respond.
The Need to Continuously Validate Security Today
Continuously validating an organization’s security is foundational in a cybersecurity program to meet various compliance standards, industry regulations, and federal mandates. Organizations must provide proof with validated artifacts and certified, independent penetration testing reports that their systems and overall environments continuously meet the requirements the organization has set for governance, risk, and compliance.
Furthermore, the benefits of continuous validation combined with penetration testing can be a force multiplier for audit-readiness, incident preparedness, and fortified defenses.
As security leaders seek new solutions to improve security outcomes and prevent breaches, they are looking at the testing aspect to improve compliance while validating security. With this Cyber Security Validation in place, everything works together as a full-stack solution. This new solution offers an exit strategy from legacy pentesting solutions for a more advanced risk management solution that accelerates outcomes for today’s modern SOC.
The Problem with Traditional Penetration Testing
Legacy penetration testing solutions are still using manual testing methods despite the availability of modern technology, like AI and automation.
Furthermore, traditional penetration testing has historically left DevOps in the dark. While integrating DevOps remediation within the lifecycle of the actual penetration test just makes good business sense – the opportunity is overlooked when working with legacy providers. This approach causes persistent delays, increased costs, and revenue loss – all the while security risks and compliance vulnerabilities that were discovered during the penetration test are left unnecessarily exposed. The obvious missed opportunity is clear – especially when security leaders can pursue a better way.
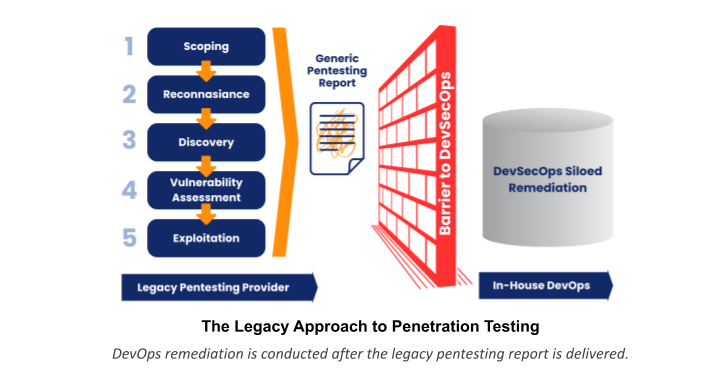
When a penetration tester discovers a critical vulnerability – shouldn’t DevOps be alerted right away? Security leaders deserve a better solution from their penetration testing investments.
What is Pen Testing as a Service (PTaaS)?
One of the most exciting innovative approaches today for security and technology leaders today is the augmented capabilities available through a qualified Pentesting as a Service (PTaaS) platform and service provider.
PTaaS is a modern approach to delivering penetration testing services. It utilizes a combination of manual human-led pentesting, AI, and automation tools and techniques that accelerate pentesting without false positives. This solution is gaining momentum, as it helps mitigate the cybersecurity skills gap being faced by security leaders at a global level. PTaaS helps technology and security leaders tap into a treasure trove of expertise to maximize their pen testing investments. With experienced, certified penetration testers available on-demand, PTaaS customers can tap into the talent they need to conduct a penetration test at any time – without the added expense of hiring expensive security practitioners.
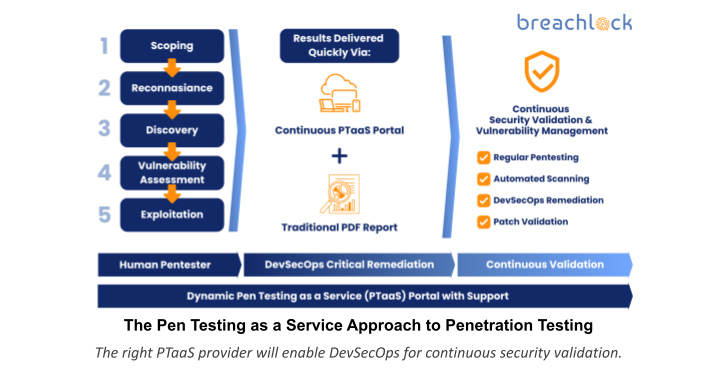
How PTaaS Works to Validate Security Continuously
Rather than a linear approach where a legacy pen test is delivered and the in-house DevOps team takes on the recommended remediations after the pen test concludes, PTaaS integrates DevOps remediation into the lifecycle of each penetration test. This enables a DevSecOps testing approach to managing cybersecurity risk – the preferred approach by CISOs to improve security maturity and cyber resilience.
Furthermore, the right PTaaS provider will offer continuous vulnerability management benefits long after the pen test has concluded within the client portal hosted via a cloud platform that includes patch retesting and automated vulnerability scanning. These benefits facilitate team collaboration with the PTaaS provider as they manage the PTaaS tools inside the platform that provide continuous security validation.
PTaaS Benefits Explained
As organizations continue to rely on technology for daily security operations, it is important to have a comprehensive understanding of potential security vulnerabilities. Pen Testing as a Service (PTaaS) gives CISOs the capabilities they need to conduct continuous pen testing to uncover weaknesses in networks, applications, and cloud systems from a certified third party that provides continuous security testing, vulnerability scanning, and insights on critical risks.
Immediate Benefits of PTaaS
The biggest benefit that CISOs can expect from selecting the right PTaaS investment is seeing security outcomes improved across teams as they get unbiased penetration testing conducted by in-house, certified human experts using industry-standard methodologies, cutting edge technology, and an advanced cloud pentesting platform to manage each PTaaS engagement.
The PTaaS model provides additional immediate benefits, including the following advantages:
- Agility
- More cost-effective than traditional in-house penetration testing
- Faster scheduling, testing efficiency, and report execution
- API integrates with DevOps ticketing management systems
- Accuracy
- Secure cloud platform provides visibility of test results
- Certified penetration testers conduct full-stack penetration tests
- AI and automation improve security testing efficiency
- Human testers validate automated results and security discoveries
- Guaranteed Zero false positives
- Reduced Total Cost of Ownership (TCO)
- Improves security outcomes and compliance-readiness affordably
- Remove duplicative vulnerability scanning and testing technologies in the security tech stack
- Replace traditional pentesting services with PTaaS continuous security testing capabilities, features, and benefits
- Scalability
- Eliminate the DevOps silo of remediation
- Real-time communications are included with client access to penetration testers
- Order pen tests on-demand and when needed
Long Term Benefits of PTaaS
Over time, when PTaaS is incorporated into a comprehensive security strategy, security leaders can greatly advance an organization’s defenses against cyber threats and strengthen overall cyber resilience.
The long-term benefits of PTaaS delivery in your organization are significant, including the benefits as follows:
- Cost Savings
- Outsource the end-to-end aspects of the pentesting process, including preventing potential scope creep
- Continuous Security Validation
- Keep Security and DevOps teams stay on top of security and compliance and enables them to rapidly respond to new vulnerabilities
- Visibility into the Adversary’s Perspective
- Get an accurate report of what adversaries can see exposed in the client’s systems with an objective and impartial perspective
- In-House Team Extension
- Tap into expertise and resources lacking in-house
- Improved Security Outcomes
- Identify risks, exposures, and weaknesses to remediate now and validate with retesting over time
- Governance, Risk, and Compliance Pentesting Management
- Enforce compliance requirements for critical regulations by conducting routine PCI-DSS pentesting, HIPAA Pentesting and GDPR Testing
- Integrated DevSecOps Remediation
- Improve remediation times with DevSecOps remediation integrated throughout all phases of the pen test, including early discovery
- Full-Stack Visibility Across Systems
- See vulnerabilities by risk and criticality across full-stack systems, including applications, devices, and networks
- Improved Team Workflows
- Increase the speed of security teams and other departments within the company with integrations for workflow ticketing
- Ability to Start the Next Pentest Fast
- Start the next penetration test quickly, and relieve backlogs that are holding back revenue-generating projects
The Right PTaaS Solution for Continuous Security Validation
Like some other newer offensive security categories, PTaaS has generated a ton of interest quickly – first with CISOs, and now, more recently with product owners and other developers with a stake in the DevSecOps process. Naturally, this has attracted a host of new options adding to the legacy options available – making the final selection of your preferred PTaaS provider more complicated.
Unlike late entrants to the PTaaS market, third party security service providers, like BreachLock, are leading the Pen Testing as a Service category. With an innovative continuous security validation solution and in-house security experts and penetration testers, BreachLock is a proven PTaaS provider that is fast, reliable, and affordable. BreachLock offers CIOs and CISOs piece of mind with a new way to meet their security validation, pentesting, and compliance requirements in half the time for half the cost of traditional solutions. Interested in learning more? Book a discovery call with BreachLock to see how their award-winning, analyst recognized PTaaS solution can work for you today.
