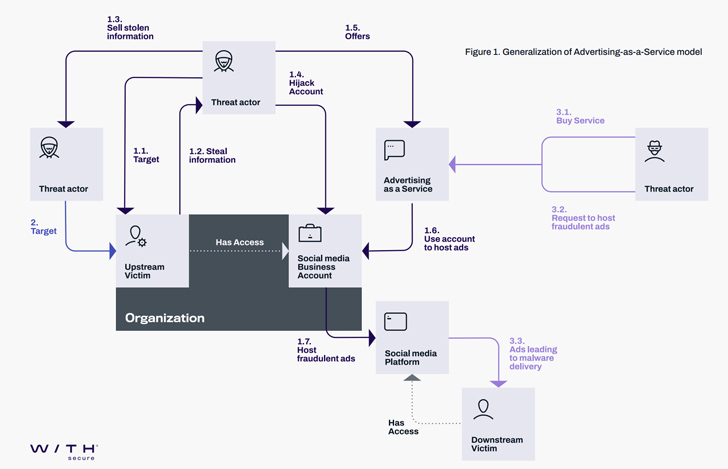
Malicious actors associated with the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms such as Meta-owned Facebook to distribute malware.
“Threat actors have long used fraudulent ads as a vector to target victims with scams, malvertising, and more,” WithSecure researcher Mohammad Kazem Hassan Nejad said. “And with businesses now leveraging the reach of social media for advertising, attackers have a new, highly-lucrative type of attack to add to their arsenal – hijacking business accounts.”
Cyber attacks targeting Meta Business and Facebook accounts have gained popularity over the past year, courtesy of activity clusters such as Ducktail and NodeStealer that are known to raid businesses and individuals operating on Facebook.
Among the methods employed by cybercriminals to gain unauthorized access to user accounts, social engineering plays a significant role.
Victims are approached through various platforms ranging from Facebook and LinkedIn to WhatsApp and freelance job portals like Upwork. Another known distribution mechanism is the use of search engine poisoning to boost bogus software such as CapCut, Notepad++, OpenAI ChatGPT, Google Bard, and Meta Threads.
An element that’s common to these groups is the abuse of URL shortener services, Telegram for command-and-control (C2), and legitimate cloud services like Trello, Discord, Dropbox, iCloud, OneDrive, and Mediafire to host the malicious payloads.

The actors behind Ducktail, for instance, leverage lures related to brand and marketing projects to infiltrate individuals and businesses that operate on Meta’s Business platform, with new attack waves employing job and recruitment-related themes to activate the infection.
In these attacks, potential targets are directed to bogus postings on Upwork and Freelancer through Facebook ads or LinkedIn InMail, which, in turn, contain a link to a booby-trapped job description file hosted on one of the aforementioned cloud storage providers, ultimately leading to the deployment of the Ducktail stealer malware.
“Ducktail malware steals saved session cookies from browsers, with code specifically tailored to take over Facebook business accounts,” Zscaler ThreatLabz researchers Sudeep Singh and Naveen Selvan noted in a parallel analysis, stating the accounts sell for anywhere between $15 to $340.
“The ‘products’ of the operation (i.e. hacked social media accounts) feed an underground economy of stolen social media accounts, where numerous vendors offer accounts priced according to their perceived usefulness for malicious activity.”
Select infection sequences observed between February and March 2023 have involved the use of shortcut and PowerShell files to download and launch the final malware, illustrating the attackers’ continued evolution of their tactics.
The experimentation also extends to the stealer, which has been updated to harvest a user’s personal information from X (formerly Twitter), TikTok Business, and Google Ads, as well as leverage the stolen Facebook session cookies to create fraudulent ads in an automated fashion and obtain elevated privileges to perform other actions.
A primary method used to takeover a victim’s compromised account is by adding their own email address to that account, subsequently changing the password and email address of the victim’s Facebook account to lock them out of the service.
“Another new feature observed in Ducktail samples since (at least) July 2023 is using RestartManager (RM) to kill processes that lock browser databases,” WithSecure said. “This capability is often found in ransomware as files that are in-use by processes or services cannot be encrypted.”
What’s more, the final payload is obscured using a loader to decrypt and execute it dynamically at runtime in what’s seen as an attempt to incorporate techniques aimed at increasing analysis complexity and detection evasion.
Some of the other methods adopted by the threat actor to hinder analysis encompass the use of uniquely generated assembly names and the reliance on SmartAssembly, bloating, and compression to obfuscate the malware.
Zscaler said it spotted cases where the group initiated contact via compromised LinkedIn accounts that belonged to users working in the digital marketing space, some of whom had more than 500 connections and 1,000 followers.
Detect, Respond, Protect: ITDR and SSPM for Complete SaaS Security
Discover how Identity Threat Detection & Response (ITDR) identifies and mitigates threats with the help of SSPM. Learn how to secure your corporate SaaS applications and protect your data, even after a breach.
Supercharge Your Skills
“The high amount of connections/followers helped lend authenticity to the compromised accounts and facilitated the social engineering process for threat actors,” the researchers said.
This also highlights the worm-like propagation of Ducktail wherein LinkedIn credentials and cookies stolen from a user who fell victim to the malware attack is used to login to their accounts and contact other targets and broaden their reach.
Ducktail is said to be one of the many Vietnamese threat actors who are leveraging shared tooling and tactics to pull off such fraudulent schemes. This also includes a Ducktail copycat dubbed Duckport, which has been active since late March 2023 and performs information stealing alongside Meta Business account hijacking.
It’s worth pointing out that the campaign that Zscaler is tracking as Ducktail is in fact Duckport, which, according to WithSecure, is a separate threat owing to the differences in the Telegram channels used for C2, the source code implementation, and the fact that both the strains have never been distributed together.
“While Ducktail has dabbled with the usage of fake branded websites as part of their social engineering efforts, it has been a common technique for Duckport,” WithSecure said.
“Instead of providing direct download links to file hosting services such as Dropbox (which may raise suspicion), Duckport sends victims links to branded sites that are related to the brand/company they’re impersonating, which then redirects them to download the malicious archive from file hosting services (such as Dropbox).”
Duckport, while based on Ducktail, also comes with novel features that expand on the information stealing and account hijacking capabilities, and also take screenshots or abuse online note-taking services as part of its C2 chain, essentially replacing Telegram as a channel to pass commands to the victim’s machine.
“The Vietnamese-centric element of these threats and high degree of overlaps in terms of capabilities, infrastructure, and victimology suggests active working relationships between various threat actors, shared tooling and TTPs across these threat groups, or a fractured and service-oriented Vietnamese cybercriminal ecosystem (akin to ransomware-as-a-service model) centered around social media platforms such as Facebook.”