A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium.
The activity has been codenamed Steal-It by Zscaler ThreatLabz.
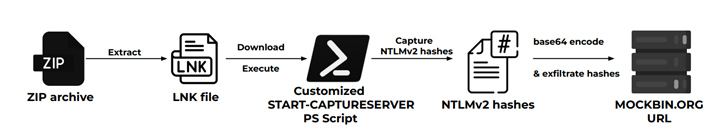
“In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang’s Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs,” security researchers Niraj Shivtarkar and Avinash Kumar said.

Nishang is a framework and collection of PowerShell scripts and payloads for offensive security, penetration testing, and red teaming.
The attacks leverage as many as five different infection chains, although they all leverage phishing emails containing ZIP archives as the starting point to infiltrate specific targets using geofencing techniques –
- NTLMv2 hash stealing infection chain, which employs a custom version of the aforementioned Start-CaptureServer PowerShell script to harvest NTLMv2 hashes
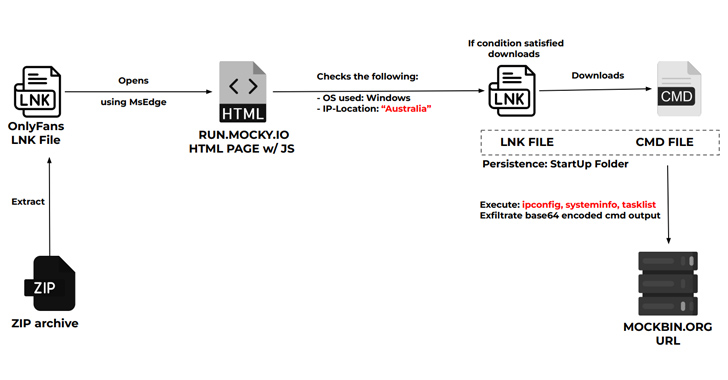
- System info stealing infection chain, which OnlyFans lures to target Australian users into downloading a CMD file that pilfers system information
- Fansly whoami infection chain, which uses explicit images of Ukrainian and Russian Fansly models to entice Polish users into downloading a CMD file that exfiltrates the results of the whoami command
- Windows update infection chain, which targets Belgium users with fake Windows update scripts designed to run commands like tasklist and systeminfo
It’s worth noting that the last attack sequence was highlighted by the Computer Emergency Response Team of Ukraine (CERT-UA) in May 2023 as part of an APT28 campaign directed against government institutions in the country.
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
Supercharge Your Skills
This raises the possibility that the Steal-It campaign could also be the work of the Russian state-sponsored threat actor.
“The threat actors’ custom PowerShell scripts and strategic use of LNK files within ZIP archives highlights their technical expertise,” the researchers said. “The persistence maintained by moving files from the Downloads to Startup folder and renaming them underscores the threat actors’ dedication to prolonged access.”