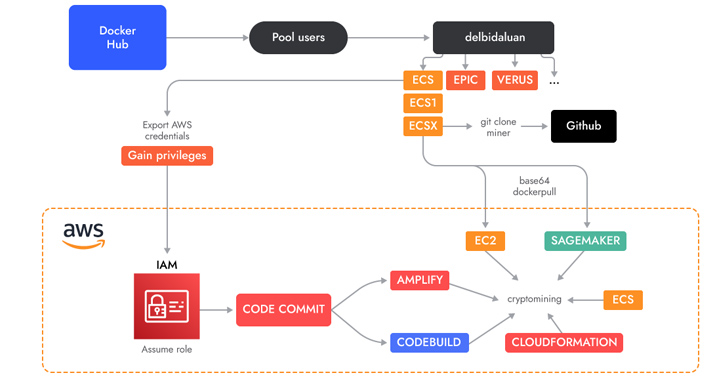
A novel cloud-native cryptojacking operation has set its eyes on uncommon Amazon Web Services (AWS) offerings such as AWS Amplify, AWS Fargate, and Amazon SageMaker to illicitly mine cryptocurrency.
The malicious cyber activity has been codenamed AMBERSQUID by cloud and container security firm Sysdig.
“The AMBERSQUID operation was able to exploit cloud services without triggering the AWS requirement for approval of more resources, as would be the case if they only spammed EC2 instances,” Sysdig security researcher Alessandro Brucato said in a report shared with The Hacker News.
“Targeting multiple services also poses additional challenges, like incident response, since it requires finding and killing all miners in each exploited service.”

Sysdig said it discovered the campaign following an analysis of 1.7 million images on Docker Hub, attributing it with moderate confidence to Indonesian attackers based on the use of Indonesian language in scripts and usernames.
Some of these images are engineered to execute cryptocurrency miners downloaded from actor-controlled GitHub repositories, while others run shell scripts targeting AWS.
A key characteristic is the abuse of AWS CodeCommit, which is used to host private Git repositories, to “generate a private repository which they then used in different services as a source.”
The repository contains the source code of an AWS Amplify app that, in turn, is leveraged by a shell script to create a Amplify web app and ultimately launch the cryptocurrency miner.
The threat actors have also been observed employing shell scripts to perform cryptojacking in AWS Fargate and SageMaker instances, incurring significant compute costs for the victims.
Sysdig estimated that AMBERSQUID could result in losses of more than $10,000 per day if it’s scaled to target all AWS regions. A further analysis of the wallet addresses used reveals that the attackers have earned more than $18,300 in revenues to date.
Identity is the New Endpoint: Mastering SaaS Security in the Modern Age
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identity is the new endpoint. Secure your spot now.
Supercharge Your Skills
This is not the first time Indonesian threat actors have been linked to cryptojacking campaigns. In May 2023, Permiso P0 Labs detailed an actor named GUI-vil which was spotted leveraging Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances to carry out crypto mining operations.
“While most financially motivated attackers target compute services, such as EC2, it is important to remember that many other services also provide access to compute resources (albeit it more indirectly),” Brucato said.
“It is easy for these services to be overlooked from a security perspective since there is less visibility compared to that available through runtime threat detection.”