When you roll out a security product, you assume it will fulfill its purpose. Unfortunately, however, this often turns out not to be the case. A new report, produced by Osterman Research and commissioned by Silverfort, reveals that MFA (Multi-Factor Authentication) and PAM (Privileged Access Management) solutions are almost never deployed comprehensively enough to provide resilience to identity threats. As well, service accounts – which are typically beyond the scope of protection of these controls – are alarmingly exposed to malicious compromise. These findings and many more can be found in “The State of the Identity Attack Surface: Insights Into Critical Protection Gaps,” the first report that analyzes organizational resilience to identity threats.
What is the “Identity Attack Surface”?
The identity attack surface is any organizational resource that can be accessed via username and password. The main way that attackers target this attack surface is through the use of compromised user credentials. In this way, the identity attack surface differs substantially from other attack surfaces. When targeting endpoints, for example, attackers have to develop innovative malware and zero-day exploits. But in the world of identity the default attack tool is legitimate usernames and passwords. And with an estimated 24B username-password combinations available on the Dark Web, this means the only work attackers need to do is gain the initial access.
But I Have MFA and PAM in Place to Prevent Attacks
Do you, though? According to the report, which summarizes findings from 600 identity security professionals surveyed around the world, the vast majority of organizations have MFA and PAM solutions in place yet remain exposed to attacks. Here’s why:
Less than 7% of organizations have MFA protection for the majority of their critical resources
One of the questions the survey asked was: What proportion of the following resources and access methods are you currently able to protect with MFA?
- Desktop logins (e.g. Windows, Mac)
- VPN and other remote connection methods
- RDP
- Command-line remote access (e.g. PowerShell, PsExec)
- SSH
- Homegrown and legacy apps
- IT infrastructure (e.g. management consoles)
- VDI
- Virtualization platforms and hypervisors (e.g. VMware, Citrix)
- Shared network drives
- OT systems
This graph summarizes the results:
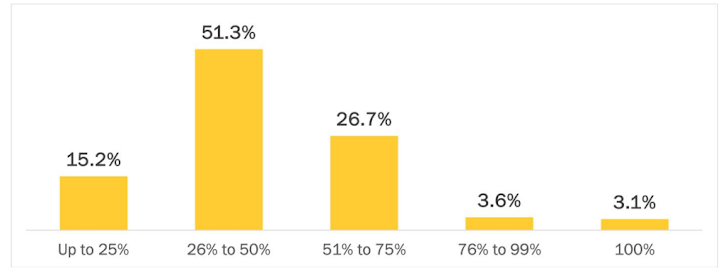
These numbers imply a critical gap, since a resource without MFA is a resource that an adversary can seamlessly access using compromised credentials. Translating this to a real-life scenario, a threat actor using command-line tool that’s not protected with MFA – such as PsExec or Remote PowerShell – will encounter no obstacles when moving across a network in order to plant a ransomware payload on multiple machines.
Only 10.2% of organizations have a fully onboarded PAM solution
PAM solutions are notorious for long, complex deployments, but how bad is it really? The report reveals the answer: It’s bad. Here is an aggregation of respondents’ answers to the question “Where are you in your PAM implementation journey?”
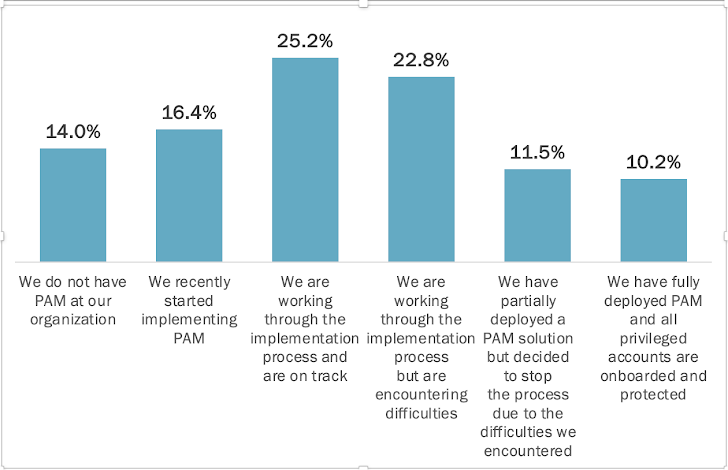
As you can see, most organizations are stuck somewhere along their PAM journey, which means at least some of their privileged users are exposed to attacks. And keep in mind that admin users are an attackers’ fastest path to your crown jewels. Failing to protect all of them is a risk no organization can afford to ignore.
78% of organizations can’t prevent malicious access with compromised service accounts
Service accounts are a well-known blind spot. Because these non-human accounts are often highly privileged yet can’t be protected by MFA – as well as the fact that they are typically undocumented and thus unmonitored – they are a prime target for adversaries.
Here are the answers to the question, “How confident are you in your ability to prevent attackers from using service accounts for malicious access in your environment?”
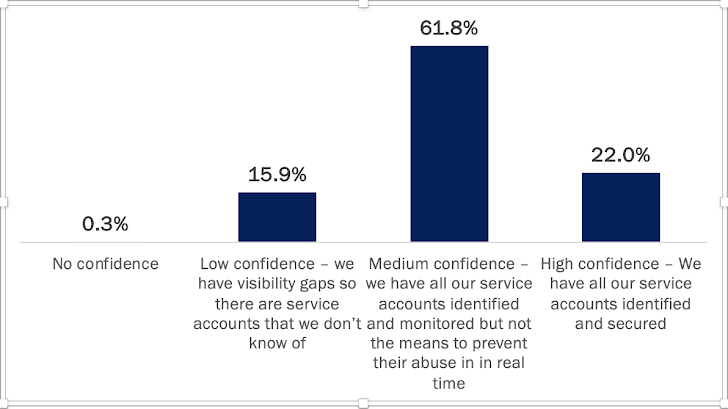
Note that the term “medium” here is a bit misleading, since the absence of real-time prevention essentially voids the security value of being able to detect an account’s compromise.
How Well Are You Protecting Your Environment’s Identity Attack Surface? Use the Maturity Model
The report goes beyond pointing out weaknesses and gaps — it offers a useful scoring model that, based on aggregated results across all the identity protection aspects, can reveal your level of resilience to identity threats.
The report found that very few organizations – as low as 6.6% – have a disciplined and implemented identity protection strategy in place. But use this model to answer the same questions and see how your organization stacks up, and also what actions you need to take.
Ready to see how resilient you are to identity threats? Access the report here.