2023 CL0P Growth
Emerging in early 2019, CL0P was first introduced as a more advanced version of its predecessor the ‘CryptoMix’ ransomware, brought about by its owner CL0P ransomware, a cybercrime organisation. Over the years the group remained active with significant campaigns throughout 2020 to 2022. But in 2023 the CL0P ransomware gang took itself to new heights and became one of the most active and successful ransomware organizations in the world.
Capitalizing on countless vulnerabilities and exploits for some of the world’s largest organizations. The presumed Russian gang took its name from the Russian word “klop,” which translates to “bed bug” and is often written as “CLOP” or “cl0p”. Once their victims’ files are encrypted, “.clop” extensions are added to their files.
CL0P’s Methods & Tactics
The CL0P ransomware gang (closely associated with the TA505. FIN11, and UNC2546 cybercrime groups) was renowned for their extremely destructive and aggressive campaigns, which targeted large organizations around the world throughout 2023. The “big game hunter” ransomware gang utilized the “steal, encrypt and leak” method on numerous large companies with a specific interest for those in the Finance, Manufacturing and Healthcare industries.
CL0P operates a Ransomware-as-a-Service model (RaaS), which frequently employs the ‘steal, encrypt, and leak’ tactics common worldwide among many ransomware affiliates. If its victims fail to meet the demands, their data is published via the gang’s Tor-hosted leak site known as ‘CL0P^_-LEAKS’. Just like many other Russian-speaking cyber gangs, their ransomware was unable to operate on devices located in the CIS (Commonwealth of Independent States).
LockBit also operates as a Ransomware-as-a-service (RaaS) model.
‘In short, this means that affiliates make a deposit to use the tool, then split the ransom payment with the LockBit group. It has been reported that some affiliates are receiving a share as high as 75%. LockBit’s operators have posted advertisements for their affiliate program on Russian-language criminal forums stating they will not operate in Russia or any CIS countries, nor will they work with English-speaking developers unless a Russian-speaking “guarantor” vouches for them.’ – ‘The Prolificacy of LockBit Ransomware’
SecurityHQ’s Global Threat Landscape2024 Forecast talked about CL0P’s resurgence in the ransomware landscape and one to be on the lookout for in 2024.
3rd Most Prolific Group 2023
After examining the data from ‘CL0P^_-LEAKS’, the threat intelligence team at SecurityHQ was able to collect data on various cybercrime gangs around the world and help visualize the extent of CL0P’s rise in activity throughout 2023. The gangs’ transition from remaining outside the topmost active ransomware groups in 2022 to securing the third most prolific in 2023 is something that should not be taken lightly.
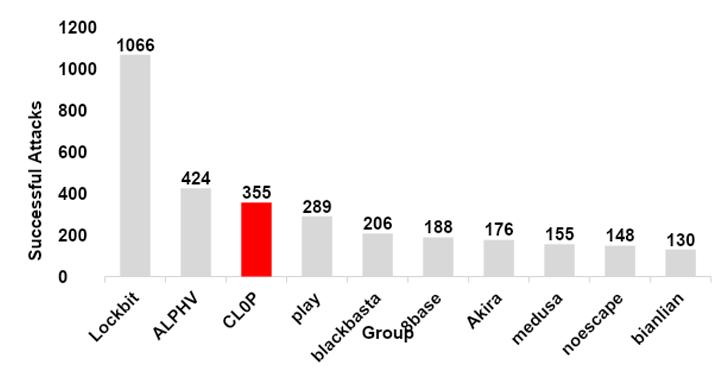 |
| ©2024 SecurityHQ, SecurityHQ Data on Threat Groups During 2023 |
Latest Activities
Over a month-long period throughout March of 2023, the CL0P ransomware gang attempted to exploit ‘Fortra GoAnywhere MFT’ zero-day vulnerability. Tracked as CVE-2023-0669, attackers were able to capitalize on unpatched versions of the software with internet access to obtain RCE. The vulnerability was patched the following day, but the group had already successfully targeted over 100 organisations.
Then, in April, Microsoft was able to identify the involvement of two ransomware gangs (CL0P and LockBit) who were exploiting the tracked CVE-2023-27350 and CVE-2023-27351. Contained inside the print management software known as PaperCut, which is a common tool used among all the large printing firms worldwide. The groups were able to exploit this vulnerability, successfully deploying the infamous TrueBot malware that had been used many months prior. A perfect target for the likes of CL0P, whose tactics have shifted from not just encrypting the files anymore but more towards stealing the data to further extort the organisations. This worked perfectly as Papercut features a “Print Archiving” tool that saves any job/document that is sent through their server.
The group’s major event came in May; the widely used MOVEit Transfer (CVE-2023-24362) and MOVEit Cloud Software (CVE-2023-35036) were actively exploited via an unknown SQL injection vulnerability. CL0P was able to capitalize on vulnerable networks and systems extremely quickly, extracting sensitive data from some of the world’s largest organizations (BBC, Ernst Young, PwC, Gen Digital, British Airways, TFL, Siemens, and many more). The group stated they had deleted all data relating to governments, military, and hospitals, but with several US government agencies being affected by the MOVEit breach, a bounty of $10 million was set in place that could help link them to a foreign agent.
Lasting Impact of Quadruple Extortion
The group has not only played a major role on the influx in ransomware activity throughout 2023 but was almost single handedly responsible for the drastic increase in the average ransomware payments.
CL0P’s operators are renowned for going to extreme lengths to get their message across. After publicly displaying the proof of the organisations breach, publishing data on their leak site and their messages being ignored, they will go straight to stakeholders and executives to ensure their demands are met. This is known as quadruple extortion.
From single to double, double to triple and now the progression to quadruple extortion, it’s fair to say ransomware groups aren’t stopping until they get what they came for. Just like the double or triple extortion, quadruple extortion adds a new layer which comes in the form of two main avenues.
- The first is DDoS attacks, which aim to shut down an organization’s online presence until the ransom is paid.
- The harassment of various stakeholders (customers, media, employees, etc.) increases pressure on the decision-makers.
Best Defense Against CL0P Group Defending Against CL0P
To defend against CLOP throughout 2024, it is recommended by SecurityHQ to
- Pay attention to your landscape and your environment. Know what is normal for your environment and what is not so you can act quickly.
- Develop and review your Incident Response Plan, with clear steps shown so that actions are set in the event of a worst-case scenario.
- Ensure that Threat Monitoring is in place to identify threats rapidly.
- Review current cyber security practices to make sure that the best practices are being used.
- Those at greater risk, for instance, those in industries specifically targeted by CLOP (Finance, Manufacturing, Healthcare), or those that hold sensitive data, should work with an MSSP to ensure that the best security practices are in place.
Threat Intelligence for the Future
SecurityHQ’s Threat Intelligence team is a cohesive global unit dedicated to Cyber Threat Intelligence. Their team is focused on researching emerging threats and tracking activities of threat actors, ransomware groups, and campaigns to ensure that they stay ahead of potential risks. Beyond their investigative work, the Intelligence team provides actionable threat intelligence and research, enriching the understanding of SecurityHQ’s customers worldwide. United by a common commitment, the SecurityHQ Threat Intelligence team delivers the insights needed to navigate the intricacies of the cyber security threat landscape confidently.
For more information on these threats, speak to an expert here. Or if you suspect a security incident, you can report an incident here.
Note: This expertly contributed article is written by Patrick McAteer, Cyber Threat Intelligence Analyst at SecurityHQ Dubai, excels in analyzing evolving cyber threats, identifying risks, and crafting actionable intelligence reports to empower proactive defense.
