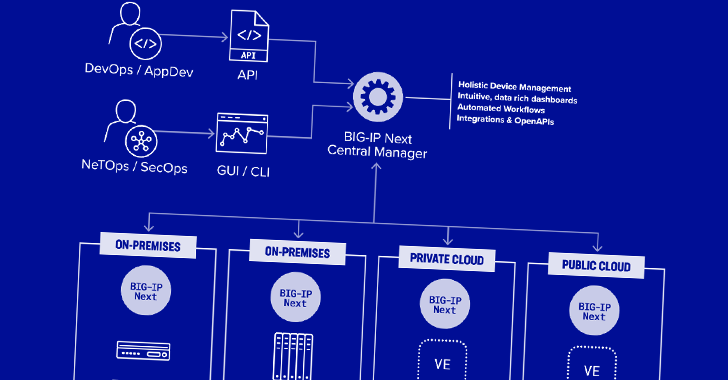
Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator accounts for persistence.
The remotely exploitable flaws “can give attackers full administrative control of the device, and subsequently allow attackers to create accounts on any F5 assets managed by the Next Central Manager,” security firm Eclypsium said in a new report.
A description of the two issues is as follows –
- CVE-2024-21793 (CVSS score: 7.5) – An OData injection vulnerability that could allow an unauthenticated attacker to execute malicious SQL statements through the BIG-IP NEXT Central Manager API
- CVE-2024-26026 (CVSS score: 7.5) – An SQL injection vulnerability that could allow an unauthenticated attacker to execute malicious SQL statements through the BIG-IP Next Central Manager API
Both the flaws impact Next Central Manager versions from 20.0.1 to 20.1.0. The shortcomings have been addressed in version 20.2.0.

Successful exploitation of the bugs can result in full administrative control of the device, enabling attackers to combine it with other flaws to create new accounts on any BIG-IP Next asset managed by the Central Manager.
What’s more, these malicious accounts would remain concealed from the Central Manager itself. This is made possible by a server-side request forgery (SSRF) vulnerability that makes it possible to invoke an undocumented API and create the accounts.
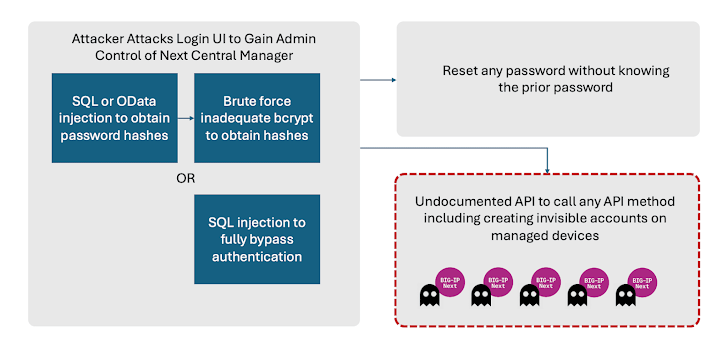
“This means that even if the admin password is reset in the Central Manager, and the system is patched, attacker access might still remain,” the supply chain security company said.
Also discovered by Eclypsium are two more weaknesses that could simply brute-force attacks against the admin passwords and permit an administrator to reset their passwords without knowledge of the prior one. An attacker could weaponize this issue to block legitimate access to the device from every account.
While there are no indications that the vulnerabilities have come under active exploitation in the wild, it’s recommended that users update their instances to the latest version to mitigate potential threats.
“Networking and application infrastructure have become a key target of attackers in recent years,” Eclypsium said. “Exploiting these highly privileged systems can give adversaries an ideal way to gain access, spread, and maintain persistence within an environment.”