The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw impacting Versa Director.
The attacks targeted four U.S. victims and one non-U.S. victim in the Internet service provider (ISP), managed service provider (MSP) and information technology (IT) sectors as early as June 12, 2024, the Black Lotus Labs team at Lumen Technologies said in a technical report shared with The Hacker News. The campaign is believed to be ongoing against unpatched Versa Director systems.
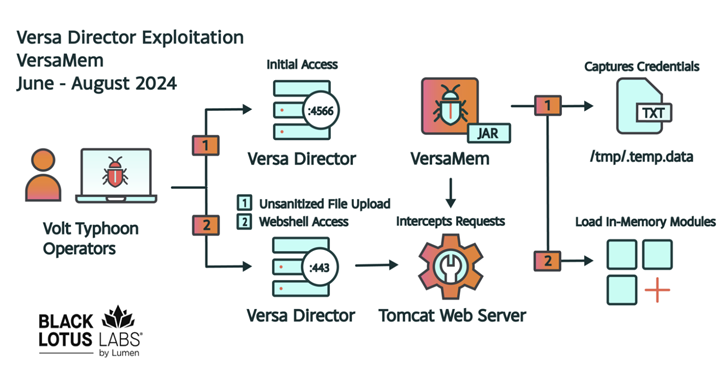
The security flaw in question is CVE-2024-39717 (CVSS score: 6.6), a file upload bug affecting Versa Director that was added to the Known Exploited Vulnerabilities (KEV) catalog last week by the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
“This vulnerability allowed potentially malicious files to be uploaded by users with Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges,” Versa said in an advisory released Monday, stating impacted customers failed to implement system hardening and firewall guidelines issued in 2015 and 2017, respectively.

The flaw essentially enables threat actors with administrator privileges to upload malicious files camouflaged as PNG image files by taking advantage of the “Change Favicon” option in the Versa Director GUI. It has been addressed in versions 22.1.4 or later.
Volt Typhoon’s targeting of Versa Networks, a secure access service edge (SASE) vendor, is not surprising and is in line with the adversary’s historical exploitation of compromised small office and home office (SOHO) network equipment to route network traffic and evade detection for extended periods of time.
The Santa Clara-based company counts Adobe, Axis Bank, Barclays, Capital One, Colt Technology Services, Infosys, Orange, Samsung, T-Mobile, and Verizon among its customers.
“Part of the attribution [to Volt Typhoon] is based on the use of SOHO devices, and the way they were employed,” Ryan English, Security researcher at Lumen’s Black Lotus Labs, told The Hacker News.
“But there was also a combination of known and observed TTPs including network infrastructure, zero-day exploitation, strategic targeting of specific sectors/victims, web shell analysis, and other confirmed overlaps of malicious activity.”
The attack chains are characterized by the exploitation of the flaw to deliver a custom-tailored web shell dubbed VersaMem (“VersaTest.png”) that’s mainly designed to intercept and harvest credentials that would enable access to downstream customers’ networks as an authenticated user, resulting in a large-scale supply chain attack.
Another noteworthy trait of the sophisticated JAR web shell is that it’s modular in nature and enables the operators to load additional Java code to run exclusively in-memory.
The earliest sample of VersaMem was uploaded to VirusTotal from Singapore on June 7, 2024. As of August 27, 2024, none of the anti-malware engines have flagged the web shell as malicious. It’s believed that the threat actors may have been testing the web shell in the wild on non-U.S. victims before deploying it to U.S. targets.
The web shell “leverages Java instrumentation and Javassist to inject malicious code into the Tomcat web server process memory space on exploited Versa Director servers,” the researchers explained.
“Once injected, the web shell code hooks Versa’s authentication functionality, allowing the attacker to passively intercept credentials in plaintext, potentially enabling downstream compromises of client infrastructure through legitimate credential use.”

“In addition, the web shell hooks Tomcat’s request filtering functionality, allowing the threat actor to execute arbitrary Java code in-memory on the compromised server while avoiding file-based detection methods and protecting their web shell, its modules and the zero-day itself.”
To counter the threat posed by the attack cluster, it’s advised to apply the necessary mitigations, block external access to ports 4566 and 4570, recursively search for PNG image files, and scan for possible network traffic originating from SOHO devices to port 4566 on Versa Director servers.
Volt Typhoon, which is also tracked as Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, and Voltzite, is an advanced persistent threat that’s known to be active for at least five years, targeting critical infrastructure facilities in the U.S. and Guam with the goal of maintaining stealthy access and exfiltrating sensitive data.
“This is a case that shows how Volt Typhoon continues to try to gain access to their ultimate victims patiently and indirectly,” English said. “Here they have targeted the Versa Director system as a means of attacking a strategic crossroads of information where they could gather credentials and access, then move down the chain to their ultimate victim.”
“Volt Typhoon’s evolution over time shows us that while an enterprise may not feel they would draw the attention of a highly skilled nation state actor, the customers that a product is meant to serve may be the real target and that makes us all concerned.”