A Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to steal money by means of fraudulent transactions.
“The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works,” Kaspersky researchers said. “This enables the attackers to keep updating their tools in order to find a way to circumvent the authorization policies, allowing them to perform their attacks.”
The cybercrime group emerged on the scene with ATM-focused malware attacks in the South American nation, providing it the ability to break into ATM machines to perform jackpotting – a type of attack aiming to dispense cash illegitimately – and clone thousands of credit cards to steal funds from the targeted bank’s customers.

Prilex’s modus operandi over the years has since evolved to take advantage of processes relating to point-of-sale (PoS) software to intercept and modify communications with electronic devices such as PIN pads, which are used to facilitate payments using debit or credit cards.
Known to be active since 2014, the operators are also adept at carrying out EMV replay attacks in which traffic from a legitimate EMV-based chip card transaction is captured and replayed to a payment processor like Mastercard, but with the transaction fields modified to include stolen card data.
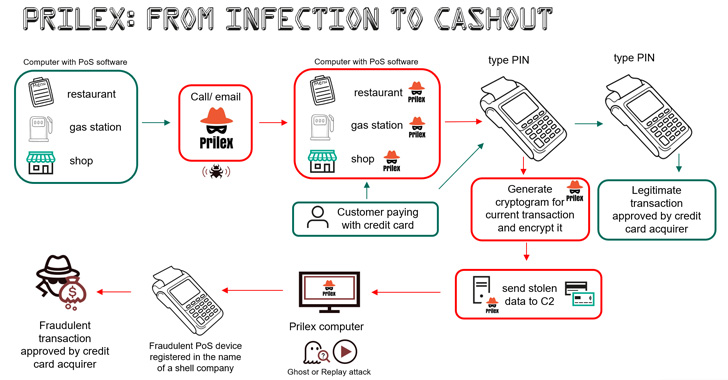
Infecting a computer with PoS software installed is a highly-targeted attack incorporating a social engineering element that allows the threat actor to deploy the malware.
“A target business may receive a call from a ‘technician’ who insists that the company needs to update its PoS software,” the researchers noted. “The fake technician may visit the target in person or request the victims to install AnyDesk and provide remote access for the ‘technician’ to install the malware.”
The latest installments spotted in 2022, however, exhibit one crucial difference in that the replay attacks have been substituted with an alternative technique to illicitly cash out funds using cryptograms generated by the victim card during the in-store payment process.
The method, called GHOST transactions, includes a stealer component that grabs all communications between the PoS software and the PIN pad used for reading the card during the transaction with the goal of obtaining the card information.
This is subsequently transmitted to a command-and-control (C2) server, permitting the threat actor to make transactions through a fraudulent PoS device registered in the name of a fake company.

Now, it’s worth pointing out that EMV chip cards use what’s called a cryptogram to secure cardholder data every time a transaction is made. This is done so as to validate the identity of the card and the approval from the card issuer, thereby reducing the risk of counterfeit transactions.
While previous versions of Prilex circumvented these security measures by monitoring the ongoing transaction to get the cryptogram and conduct a replay attack using the collected “signature,” the GHOST attack requests for new EMV cryptograms that are put to use to complete the rogue transactions.
Also baked into the malware is a backdoor module that’s engineered to debug the PoS software behavior and make changes on the fly. Other backdoor commands authorize it to terminate processes, start and stop screen captures, download arbitrary files from the C2 server, and execute commands using CMD.
Prilex is “dealing directly with the PIN pad hardware protocol instead of using higher level APIs, doing real-time patching in target software, hooking operating system libraries, messing with replies, communications and ports, and switching from a replay-based attack to generate cryptograms for its GHOST transactions even from credit cards protected with CHIP and PIN technology,” the researchers said.