DevOps platform CircleCI on Wednesday urged its customers to rotate all their secrets following an unspecified security incident.
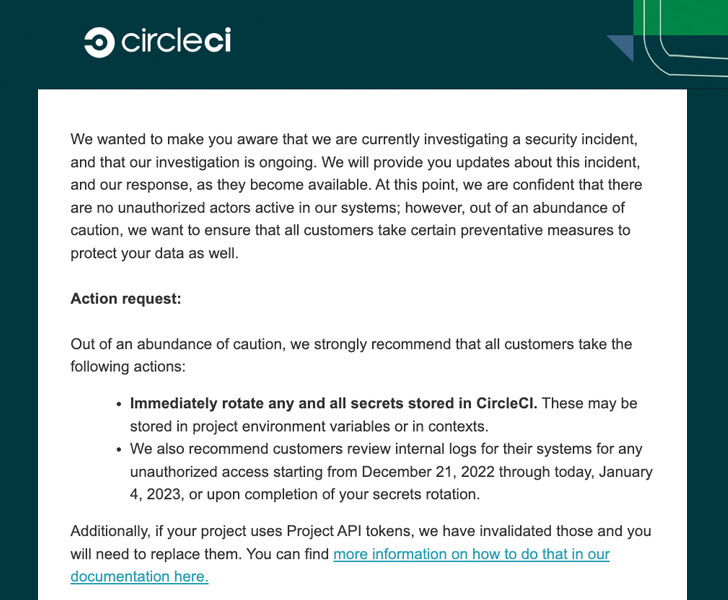
The company said an investigation is currently ongoing, but emphasized that “there are no unauthorized actors active in our systems.” Additional details are expected to be shared in the coming days.
“Immediately rotate any and all secrets stored in CircleCI,” CircleCI’s chief technology officer, Rob Zuber, said in a terse advisory. “These may be stored in project environment variables or in contexts.”
CircleCI is also recommending users to review internal logs for signs of any unauthorized access starting from December 21, 2022, to January 4, 2023, or until when the secrets are rotated.
The software development service did not disclose any further specifics about the breach, but said it has also invalidated all Project API tokens and that they need to be replaced.
The disclosure comes weeks after the company announced that it had released reliability updates to the service on December 21, 2022, to resolve underlying “systemic issues.”
It’s also the latest breach to hit CircleCI in recent years. The company, in September 2019, revealed “unusual activity” related to a third-party analytics vendor that resulted in unauthorized access to usernames and email addresses associated with GitHub and Bitbucket.
Then last year, it alerted users that fake CircleCI email notifications were being used to steal GitHub credentials and two-factor authentication (2FA) codes.
Slack’s GitHub Code Repositories Stolen
It’s just not CircleCI, as Slack disclosed on December 31, 2022, that it became aware of a security issue that entailed unauthorized access to a subset of its source code repositories on GitHub.
The issue, which came to light on December 29, 2022, resulted in the theft of a limited number of Slack employee tokens that were then used to access its GitHub repository, ultimately permitting the adversary to download the source code.
Slack, however, said no customer action is required and that the breach was quickly contained. The credentials have since been invalidated.
“No downloaded repositories contained customer data, means to access customer data, or Slack’s primary codebase,” the Salesforce-owned company said. “The threat actor did not access other areas of Slack’s environment, including the production environment, and they did not access other Slack resources or customer data.”
The instant messaging service did not share more information on how the employee tokens were stolen, but stressed the “unauthorized access did not result from a vulnerability inherent to Slack.”
