The maintainers of the Cacti open-source network monitoring and fault management framework have addressed a dozen security flaws, including two critical issues that could lead to the execution of arbitrary code.
The most severe of the vulnerabilities are listed below –
- CVE-2024-25641 (CVSS score: 9.1) – An arbitrary file write vulnerability in the “Package Import” feature that allows authenticated users having the “Import Templates” permission to execute arbitrary PHP code on the web server, resulting in remote code execution
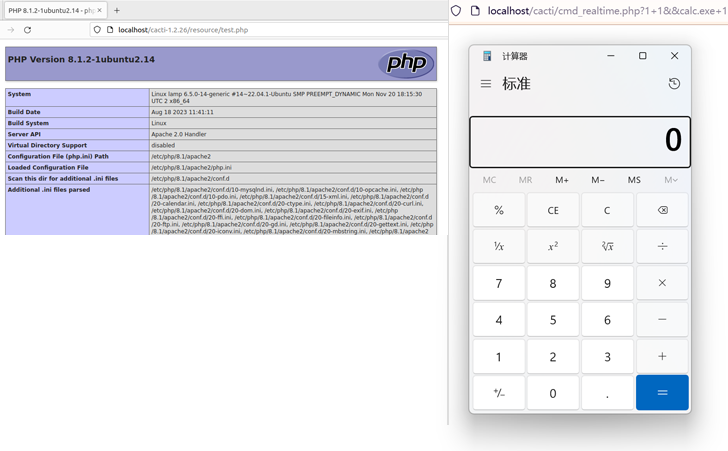
- CVE-2024-29895 (CVSS score: 10.0) – A command injection vulnerability allows any unauthenticated user to execute arbitrary command on the server when the “register_argc_argv” option of PHP is On
Also addressed by Cacti are two other high-severity flaws that could lead to code execution via SQL injection and file inclusion –
- CVE-2024-31445 (CVSS score: 8.8) – An SQL injection vulnerability in api_automation.php that allows authenticated users to perform privilege escalation and remote code execution
- CVE-2024-31459 (CVSS score: N/A) – A file inclusion issue in the “lib/plugin.php” file that could be combined with SQL injection vulnerabilities to result in remote code execution
It’s worth noting that 10 out of the 12 flaws, with the exception of CVE-2024-29895 and CVE-2024-30268 (CVSS score: 6.1), impact all versions of Cacti, including and prior to 1.2.26. They have been addressed in version 1.2.27 released on May 13, 2024. The two other flaws affect the development versions 1.3.x.

The development comes more than eight months after the disclosure of another critical SQL injection vulnerability (CVE-2023-39361, CVSS score: 9.8) that could permit an attacker to obtain elevated permissions and execute malicious code.
In early 2023, a third critical flaw tracked as CVE-2022-46169 (CVSS score: 9.8) came under active exploitation in the wild, allowing threat actors to breach internet-exposed Cacti servers to deliver botnet malware such as MooBot and ShellBot.
With proof-of-concept (PoC) exploits publicly available for these shortcomings (in the respective GitHub advisories), it’s recommended that users take steps to update their instances to the latest version as soon as possible to mitigate potential threats.
