The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign.
The intrusion set, attributed to a threat actor tracked by the authority as UAC-0063 since 2021, leverages phishing lures to deploy a variety of malicious tools on infected systems. The origins of the hacking crew are presently unknown.
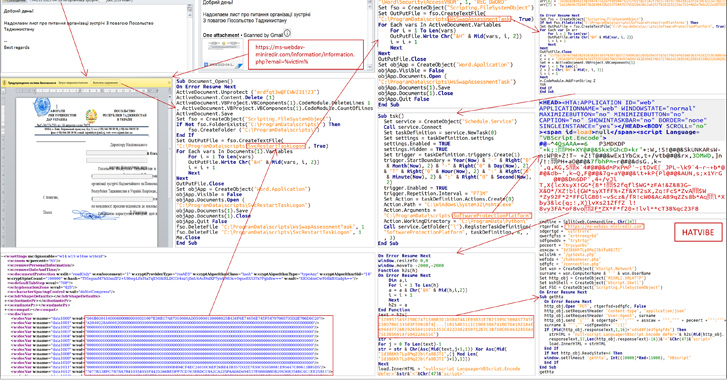
In the attack chain described by the agency, the emails targeted an unspecified ministry and purported to be from the Embassy of Tajikistan in Ukraine. It’s suspected that the messages were sent from a previously compromised mailbox.
The emails come attached with a Microsoft Word document that, upon enabling macros, launches an encoded VBScript called HATVIBE, which is then used to drop additional malware.
This includes a keylogger (LOGPIE), a Python-based backdoor capable of running commands sent from a remote server (CHERRYSPY), and a tool focused on exfiltrating files with specific extensions (STILLARCH or DownEx).
It’s worth noting that DownEx was recently documented by Bitdefender as being used by an unknown actor in highly targeted attacks aimed at government entities in Kazakhstan and Afghanistan.
“Additional study of the infrastructure and related files made it possible to conclude that among the objects of interest of the group are organizations from Mongolia, Kazakhstan, Kyrgyzstan, Israel, [and] India,” CERT-UA said.
The findings show that some threat actors are still employing macro-based malware despite Microsoft disabling the feature by default in Office files downloaded from the web.
That said, Microsoft’s restrictions have led several attack groups to experiment and adapt their attack chains and payload delivery mechanisms to include uncommon file types (CHM, ISO, LNK, VHD, XLL, and WSF) and techniques like HTML smuggling.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
Save My Seat!
Enterprise security firm Proofpoint said it observed multiple initial access brokers (IABs) – actors who infiltrate major targets and then sell that access to other cybercriminals for profit – using PDF and OneNote files starting in December 2022.
“The experimentation with and regular pivoting to new payload delivery techniques by tracked threat actors, especially IABs, is vastly different from attack chains observed prior to 2022 and heralds a new normal of threat activity,” the company said.
“No longer are the most experienced cybercriminal actors relying on one or a few techniques, but rather are frequently developing and iterating new TTPs. The rapid rate of change for many threat actors suggests they have the time, capability, and understanding of the threat landscape to rapidly develop and execute new techniques.”