A recently discovered malware builder called Quantum Builder is being used to deliver the Agent Tesla remote access trojan (RAT).
“This campaign features enhancements and a shift toward LNK (Windows shortcut) files when compared to similar attacks in the past,” Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar said in a Tuesday write-up.

Sold on the dark web for €189 a month, Quantum Builder is a customizable tool for generating malicious shortcut files as well as HTA, ISO, and PowerShell payloads to deliver next-stage malware on the targeted machines, in this case Agent Tesla.
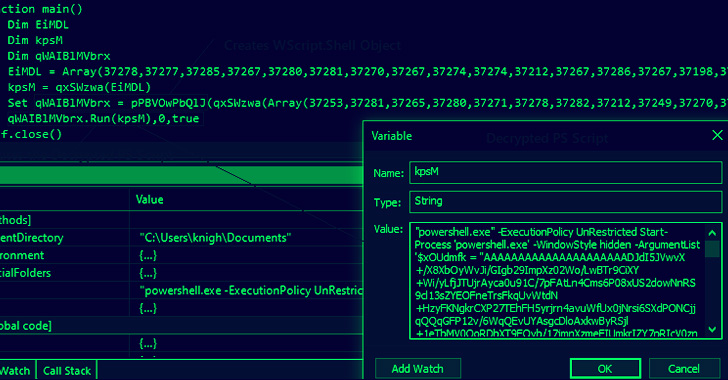
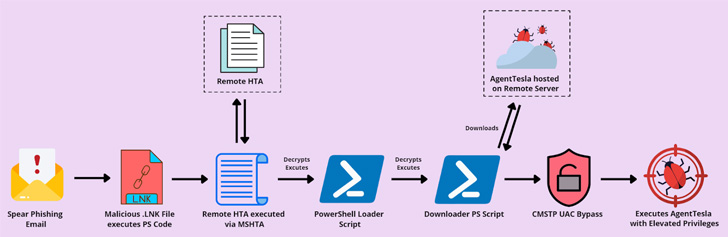
The multi-stage attack chain starts with a spear-phishing containing a GZIP archive attachment that includes a shortcut designed to execute PowerShell code responsible for launching a remote HTML application (HTA) using MSHTA.
The phishing emails purport to be an order confirmation message from a Chinese supplier of lump and rock sugar, with the LNK file masquerading as a PDF document.
The HTA file, in turn, decrypts and executes another PowerShell loader script, which acts as a downloader for fetching the Agent Tesla malware and executing it with administrative privileges.
In a second variant of the infection sequence, the GZIP archive is replaced by a ZIP file, while also adopting further obfuscation strategies to camouflage the malicious activity.

Quantum Builder has witnessed a surge in usage in recent months, with threat actors using it to distribute a variety of malware, such as RedLine Stealer, IcedID, GuLoader, RemcosRAT, and AsyncRAT.
“Threat actors are continuously evolving their tactics and making use of malware builders sold on the cybercrime marketplace,” the researchers said.
“This Agent Tesla campaign is the latest in a string of attacks in which Quantum Builder has been used to create malicious payloads in campaigns against various organizations.”