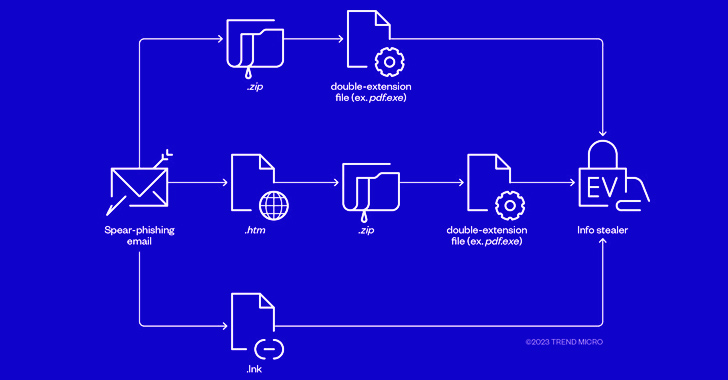
The threat actors behind RedLine and Vidar information stealers have been observed pivoting to ransomware through phishing campaigns that spread initial payloads signed with Extended Validation (EV) code signing certificates.
“This suggests that the threat actors are streamlining operations by making their techniques multipurpose,” Trend Micro researchers said in a new analysis published this week.
In the incident investigated by the cybersecurity company, an unnamed victim is said to have first received a piece of info stealer malware with EV code signing certificates, followed by ransomware using the same delivery technique.
In the past, QakBot infections have leveraged samples signed with valid code signing certificates to bypass security protections.
The attacks start with phishing emails that employ well-worn lures to trick victims into running malicious attachments that masquerade as PDF or JPG images but are actually executables that jump-start the compromise upon running.

While the campaign targeting the victim delivered stealer malware in July, a ransomware payload made its way in early August after receiving an email message containing a bogus TripAdvisor complaint email attachment (“TripAdvisor-Complaint.pdf.htm”), triggering a sequence of steps that culminated in the deployment of ransomware.
“At this point, it is worth noting that unlike the samples of the info stealer we investigated, the files used to drop the ransomware payload did not have EV certificates,” the researchers said.
“However, the two originate from the same threat actor and are spread using the same delivery method. We can therefore assume a division of labor between the payload provider and the operators.”
The development comes as IBM X-Force discovered new phishing campaigns spreading an improved version of a malware loader named DBatLoader, which was used as a conduit to distribute FormBook and Remcos RAR earlier this year.
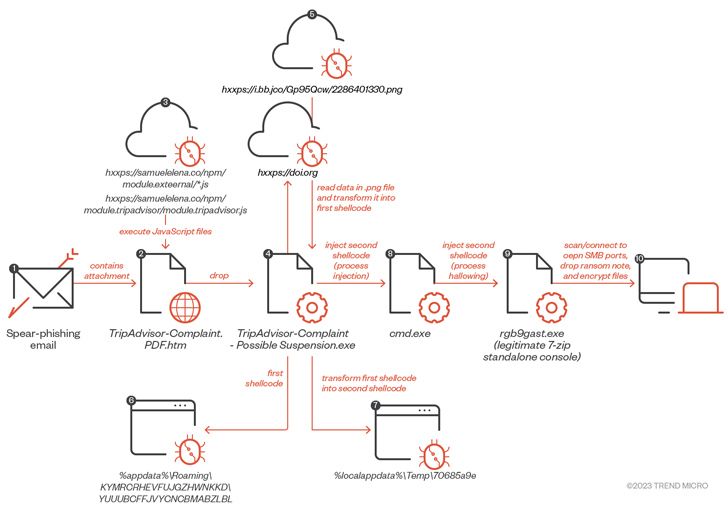
DBatLoader’s new capabilities facilitate UAC bypass, persistence, and process injection, indicating that it’s being actively maintained to drop malicious programs that can collect sensitive information and enable remote control of systems.
The recent set of attacks, detected since late June, are engineered to also deliver commodity malware such as Agent Tesla and Warzone RAT. A majority of the email messages have singled out English speakers, although emails in Spanish and Turkish have also been spotted.
“In several observed campaigns the threat actors leveraged sufficient control over the email infrastructure to enable malicious emails to pass SPF, DKIM, and DMARC email authentication methods,” the company said.
“A majority of campaigns leveraged OneDrive to stage and retrieve additional payloads, with a small fraction otherwise utilizing transfer[.]sh or new/compromised domains.”
Identity is the New Endpoint: Mastering SaaS Security in the Modern Age
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identity is the new endpoint. Secure your spot now.
Supercharge Your Skills
In related news, Malwarebytes revealed that a new malvertising campaign is targeting users who are searching for Cisco’s Webex video conferencing software on search engines like Google to redirect them to a fake website that propagates the BATLOADER malware.
BATLOADER, for its part, establishes contact with a remote server to download a second-stage encrypted payload, which is another known stealer and keylogger malware referred to as DanaBot.
A novel technique adopted by the threat actor is the use of tracking template URLs as a filtering and redirection mechanism to fingerprint and determine potential victims of interest. Visitors who don’t meet the criteria (e.g., requests originating from a sandboxed environment) are directed to the legitimate Webex site.
“Because the ads look so legitimate, there is little doubt people will click on them and visit unsafe sites,” Jérôme Segura, director of threat intelligence at Malwarebytes, said.
“The type of software being used in those ads indicate that threat actors are interested in corporate victims that will provide them with credentials useful for further network ‘pentesting’ and, in some cases, ransomware deployment.”