Government entities and large organizations have been targeted by an unknown threat actor by exploiting a security flaw in Fortinet FortiOS software to result in data loss and OS and file corruption.
“The complexity of the exploit suggests an advanced actor and that it is highly targeted at governmental or government-related targets,” Fortinet researchers Guillaume Lovet and Alex Kong said in an advisory last week.
The zero-day flaw in question is CVE-2022-41328 (CVSS score: 6.5), a medium security path traversal bug in FortiOS that could lead to arbitrary code execution.
“An improper limitation of a pathname to a restricted directory vulnerability (‘path traversal’) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands,” the company noted.
The shortcoming impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. Fixes are available in versions 6.4.12, 7.0.10, and 7.2.4 respectively.
The disclosure comes days after Fortinet released patches to address 15 security flaws, including CVE-2022-41328 and a critical heap-based buffer underflow issue impacting FortiOS and FortiProxy (CVE-2023-25610, CVSS score: 9.3).
According to the Sunnyvale-based company, multiple FortiGate devices belonging to an unnamed customer suffered from a “sudden system halt and subsequent boot failure,” indicating an integrity breach.
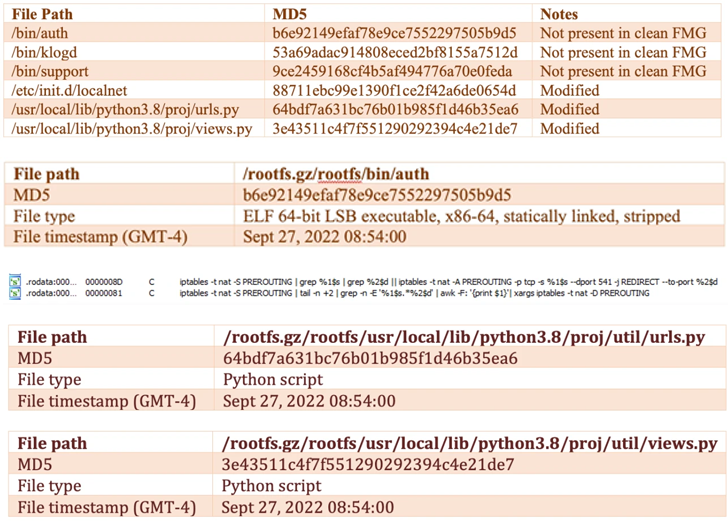
Further analysis of the incident revealed that the threat actors modified the device’s firmware image to include a new payload (“/bin/fgfm”) such that it’s always launched before the booting process began.
The /bin/fgfm malware is designed to establish contact with a remote server to download files, exfiltrate data from the compromised host, and grant remote shell access.
Additional changes introduced to the firmware are said to have provided the attacker with persistent access and control, not to mention even disable firmware verification at startup.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
RESERVE YOUR SEAT
Fortinet said the attack was highly targeted, with evidence pointing to governmental or government-affiliated organizations.
Given the complexity of the exploit, it’s suspected that the attacker has a “deep understanding of FortiOS and the underlying hardware” and possesses advanced capabilities to reverse engineer different aspects of the FortiOS operating system.
It’s not immediately clear if the threat actor has any connections to another intrusion set that was observed weaponizing a flaw in FortiOS SSL-VPN (CVE-2022-42475) earlier this January to deploy a Linux implant.
