Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network (MPN) accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to breach organizations’ cloud environments and steal email.
“The applications created by these fraudulent actors were then used in a consent phishing campaign, which tricked users into granting permissions to the fraudulent apps,” the tech giant said. “This phishing campaign targeted a subset of customers primarily based in the U.K. and Ireland.”
Consent phishing is a social engineering attack wherein users are tricked into granting permissions to malicious cloud applications, which can then be weaponized to gain access to legitimate cloud services and sensitive user data.
The Windows maker said it became aware of the campaign on December 15, 2022. It has since alerted affected customers via email, with the company noting that the threat actors abused the consent to exfiltrate mailboxes.
On top of that, Microsoft said it implemented additional security measures to improve the vetting process associated with the Microsoft Cloud Partner Program (formerly MPN) and minimize the potential for fraud in the future.
The disclosure coincides with a report released by Proofpoint about how threat actors have successfully exploited Microsoft’s “verified publisher” status to infiltrate the cloud environments of organizations.
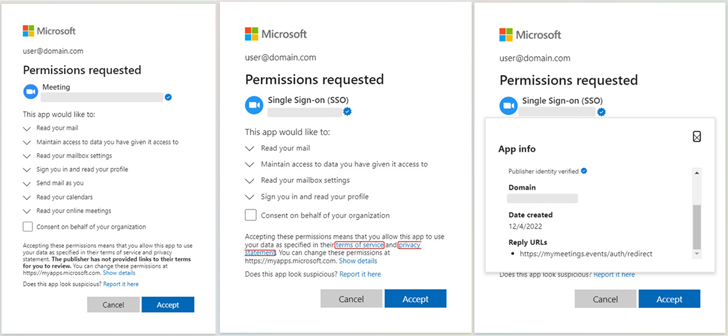
What’s notable about the campaign is that by mimicking popular brands, it was also successful at fooling Microsoft in order to gain the blue verified badge. “The actor used fraudulent partner accounts to add a verified publisher to OAuth app registrations they created in Azure AD,” the company explained.
These attacks, which were first observed on December 6, 2022, employed lookalike versions of legitimate apps like Zoom to deceive targets into authorizing access and facilitate data theft. Targets included financial, marketing, managers, and senior executives.
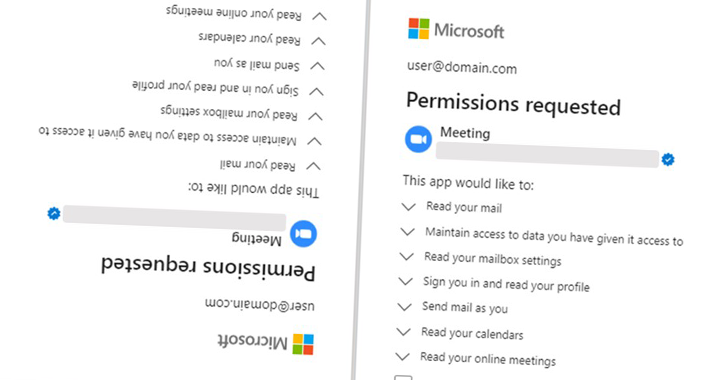
Proofpoint noted the malicious OAuth apps had “far-reaching delegated permissions” such as reading emails, adjusting mailbox settings, and gaining access to files and other data connected to the user’s account.
It also said that unlike a previous campaign that compromised existing Microsoft verified publishers to take advantage of OAuth app privileges, the latest attacks are designed to impersonate legitimate publishers to become verified and distribute the rogue apps.
Two of the apps in question were named “Single Sign-on (SSO),” while the third app was called “Meeting” in an attempt to masquerade as video conferencing software. All three apps, created by three different publishers, targeted the same companies and leveraged the same attacker-controlled infrastructure.
“The potential impact to organizations includes compromised user accounts, data exfiltration, brand abuse of impersonated organizations, business email compromise (BEC) fraud, and mailbox abuse,” the enterprise security firm said.
The campaign is said to have come to an end on December 27, 2022, after Proofpoint informed Microsoft of the attack on December 20 and the apps were disabled.
The findings demonstrate the sophistication that has gone into mounting the attack, not to mention bypass Microsoft’s security protections and misuse the trust users place in enterprise vendors and service providers.
This is not the first time bogus OAuth apps have been used to target Microsoft’s cloud services. In January 2022, Proofpoint detailed another threat activity dubbed OiVaVoii that targeted high-level executives to seize control of their accounts.
Then in September 2022, Microsoft revealed that it dismantled an attack that made use of rogue OAuth applications deployed on compromised cloud tenants to ultimately seize control of Exchange servers and distribute spam.