Threat actors are leveraging digital document publishing (DDP) sites hosted on platforms like FlipSnack, Issuu, Marq, Publuu, RelayTo, and Simplebooklet for carrying out phishing, credential harvesting, and session token theft, once again underscoring how threat actors are repurposing legitimate services for malicious ends.
“Hosting phishing lures on DDP sites increases the likelihood of a successful phishing attack, since these sites often have a favorable reputation, are unlikely to appear on web filter blocklists, and may instill a false sense of security in users who recognize them as familiar or legitimate,” Cisco Talos researcher Craig Jackson said last week.
While adversaries have used popular cloud-based services such as Google Drive, OneDrive, Dropbox, SharePoint, DocuSign, and Oneflow to host phishing documents in the past, the latest development marks an escalation designed to evade email security controls.

DDP services allow users to upload and share PDF files in a browser-based interactive flipbook format, adding page flip animations and other skeuomorphic effects to any catalog, brochure, or magazine.
Threat actors have been found to abuse the free tier or a no-cost trial period offered by these services to create multiple accounts and publish malicious documents.
Besides exploiting their favorable domain reputation, the attackers take advantage of the fact that DDP sites facilitate transient file hosting, thereby allowing published content to automatically become unavailable after a predefined expiration date and time.
What’s more, productivity features baked into DDP sites like Publuu could act as a deterrent, preventing the extraction and detection of malicious links in phishing messages.
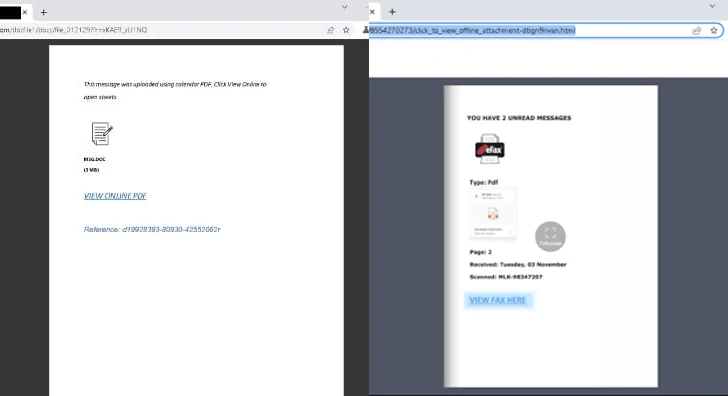
In the incidents analyzed by Cisco Talos, DDP sites are integrated into the attack chain in the secondary or intermediate stage, typically by embedding a link to a document hosted on a legitimate DDP site in a phishing email.
The DDP-hosted document serves as a gateway to an external, adversary-controlled site either directly by clicking on a link included in the decoy file, or through a series of redirects that also require solving CAPTCHAs to thwart automated analysis efforts.

The final landing page is a bogus site mimicking the Microsoft 365 login page, thus allowing the attackers to steal credentials or session tokens.
“DDP sites could represent a blind spot for defenders, because they are unfamiliar to trained users and unlikely to be flagged by email and web content filtering controls,” Jackson said.
“DDP sites create advantages for threat actors seeking to thwart contemporary phishing protections. The same features and benefits that attract legitimate users to these sites can be abused by threat actors to increase the efficacy of a phishing attack.”
