Traditional perimeter-based security has become costly and ineffective. As a result, communications security between people, systems, and networks is more important than blocking access with firewalls. On top of that, most cybersecurity risks are caused by just a few superusers – typically one out of 200 users. There’s a company aiming to fix the gap between traditional PAM and IdM solutions and secure your one out of 200 users – SSH Communications Security.
Your Privileged Access Management (PAM) and Identity Management (IdM) should work hand in hand to secure your users’ access and identities – regular users and privileged users alike. But traditional solutions struggle to achieve that.
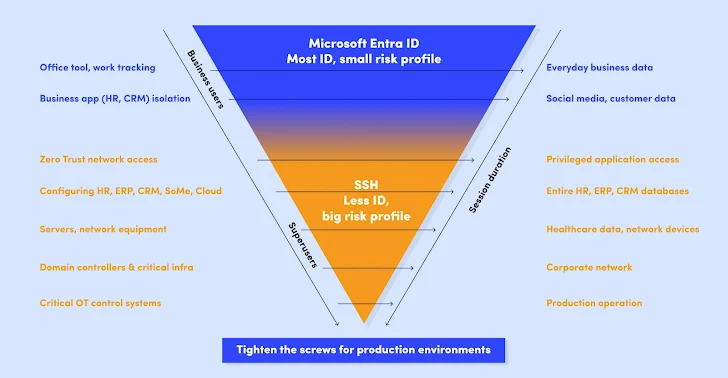 |
| Microsoft Entra manages all identities and basic-level access. With increasing criticality of targets and data, the session duration decreases, and additional protection is necessary. That’s where SSH Communications Security helps |
Let’s look at what organizations need to understand about PAM and IdM and how you can bridge and future-proof your PAM and IdM.
PIM, PAM, IAM – you need all three of them
Privileged Identity Management (PIM), Privileged Access Management (PAM), and Identity and Access Management (IAM) – all three are closely connected, and you need all three of them to effectively manage and secure your digital identities, users and access.
Let’s quickly review what PIM, PAM, and IAM focus on:
Not all digital identities are created equal – superusers need super protection
Think about this: Your typical user probably needs access to regular office tools, like your CRM or M365. They don’t need access to any of your critical assets.
The identity verification process should correspond to this. A regular user needs to be verified with strong authentication methods, e.g. Microsoft Entra ID, but there’s usually no need to go beyond that.
These typical users form the majority of your users, up to 99,5% of them.
On the other hand, you have your privileged high-impact users – there’s only a small number of them (typically around one in 200 users), but the power and risks they carry are huge because they can access your critical data, databases, infrastructures, and networks.
Similarly, appropriate identity verification procedures should apply. In the case of your high-impact users, you need access controls that go beyond strong identity-based authentication.
Enter the Zero Trust – Borderless, Passwordless, Keyless and Biometric Future
Traditional solutions are not enough to bridge your PAM and IdM. They just can’t handle the security that you need to protect your critical assets. Nor can they offer effective and future-proof security controls for access and identities of your typical users as well as high-impact users.
The future of cybersecurity is borderless, passwordless, keyless, biometric, and Zero Trust.
This means that you need a future-proof cybersecurity model with no implicitly trusted users, connections, applications, servers, or devices. On top of that, you need an additional layer of security with passwordless, keyless, and biometric authentication.
Learn the importance of implementing the passwordless and keyless approach into your cybersecurity from the whitepaper provided by SSH Communications Security. Download the whitepaper here ➜
