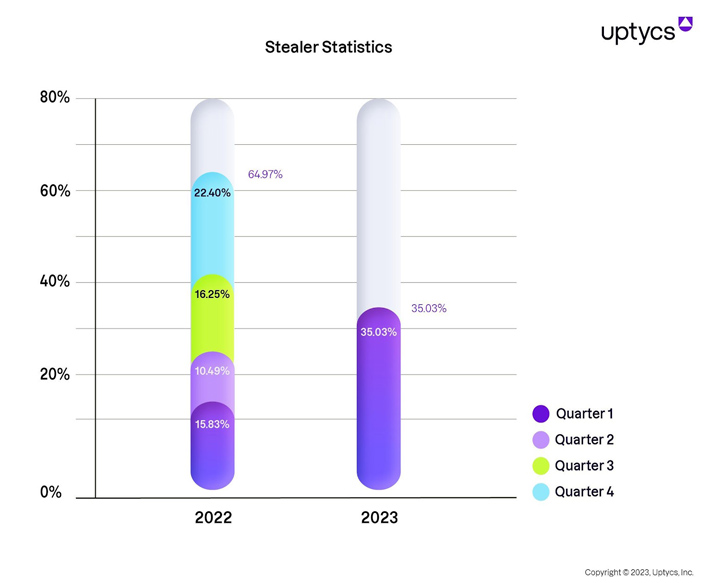
A new study conducted by Uptycs has uncovered a stark increase in the distribution of information stealing (a.k.a. infostealer or stealer) malware. Incidents have more than doubled in Q1 2023, indicating an alarming trend that threatens global organizations.
According to the new Uptycs’ whitepaper, Stealers are Organization Killers, a variety of new info stealers have emerged this year, preying on Windows, Linux, and macOS systems.
Telegram has notably been used extensively by these malware authors for command, control, and data exfiltration.
What is a Stealer?
A stealer is a type of malware that targets its victim by stealing sensitive information that can include passwords, login credentials, and other personal data. After collecting such data, the stealer sends it to the threat actor’s command and control (C2) system.
RedLine and Vidar, two well-known stealers, took advantage of log-providing services to infiltrate private systems. RedLine primarily targets credentials and cryptocurrency wallets on Windows systems, as well as browser information, FTP connections, game chat launchers, and OS data. Vidar relies on delivery methods such as phishing emails and cracked software for dissemination. Along with Racoon, it has been involved in a Google Ads malvertising operation that targets users looking for popular applications.
In one of the biggest attacks in 2022, Uber fell victim to an attack by a threat actor using the Racoon stealer. The attacker tricked victims into clicking on a fake two-factor authentication notification, compromising their systems. With access to Uber’s VPN, the attacker infiltrated the company’s internal network resources. They were able to escalate account privileges by exploiting the company’s access management service. As a result, they gained access to various Uber resources, including AWS, Duo, GSuite, OneLogin, Slack, VMware, and Windows.
The notorious Raccoon stealer malware has recently struck India, setting its sights on eight central government entities, including the Income Tax Department and central paramilitary forces. Through a malicious campaign, attackers successfully infiltrated computer systems, causing significant harm to these important institutions.
Unveiling the Modus Operandi of Infostealers
The cybersecurity world is fraught with sophisticated threats. Among the most dangerous are information stealers, capable of extracting and leaking sensitive data from individual and corporate networks. Their stealthy operations pose a significant challenge for detection and mitigation.
In Stealers are Organization Killers, Uptycs researchers present an in-depth analysis of the operational structure of the infostealer underground, the propagation methods, and the potential damage they can inflict on organizations.
Bolster Security Defenses Against Stealers
Knowledge is your organization’s strongest shield against cyber threats. Understanding the patterns and tactics used by these threat actors can fortify your defenses against potential breaches.
Uptycs’ innovative platform provides a unified solution to tackle this challenge. It prioritizes your responses to threats, vulnerabilities, and misconfigurations across your modern attack surface, all from a single UI. The platform’s ability to tie together threat activity as it traverses on-prem and cloud boundaries results in a more cohesive enterprise-wide security posture.
Uptycs: A Unified Solution for Evolving Cyber Threats
With the changing threat landscape, a piecemeal approach to security is no longer effective. Uptycs’ unified approach connects insights across your modern attack surface and brings teams together to solve key security and compliance challenges.
The Uptycs Detection Cloud integrates a Google-like search capability, allowing you to explore MITRE ATT&CK chains, create YARA rules, and investigate live and historical states, thereby providing a comprehensive solution to cybersecurity threats.
The whitepaper elaborates on the various strategies that can be implemented to mitigate the risks posed by information stealers. It serves as a treasure trove of actionable tips that can elevate the security posture of your organization.
Download Stealers are Organization Killers for an in-depth analysis of these stealers, complete with detailed diagrams and figures.
Ready to Elevate Your Cybersecurity Strategy?
The evolving tactics of threat actors necessitate constant vigilance and adaptation. This whitepaper equips infosec professionals with the knowledge and strategies needed to stay one step ahead of these threats.
If you’re committed to fortifying your organization’s defenses and wish to gain a deeper understanding of the cyber threats that you’re up against, this whitepaper is an indispensable resource. Don’t miss out on this opportunity to shift up your cybersecurity with Uptycs.
