Hackers with ties to the Iranian government have been linked to an ongoing social engineering and credential phishing campaign directed against human rights activists, journalists, researchers, academics, diplomats, and politicians working in the Middle East.
At least 20 individuals are believed to have been targeted, Human Rights Watch (HRW) said in a report published Monday, attributing the malicious activity to an adversarial collective tracked as APT42, which is known to share overlaps with Charming Kitten (aka APT35 or Phosphorus).
The campaign resulted in the compromise of email and other sensitive data belonging to three of the targets. This included a correspondent for a major U.S. newspaper, a women’s rights defender based in the Gulf region, and Nicholas Noe, a Lebanon-based advocacy consultant for Refugees International.

The digital break-in entailed gaining access to their emails, cloud storage, calendars, and contacts, as well as exfiltrating the entire data associated with their Google accounts in the form of archive files through Google Takeout.
“Iran’s state-backed hackers are aggressively using sophisticated social engineering and credential harvesting tactics to access sensitive information and contacts held by Middle East-focused researchers and civil society groups,” Abir Ghattas, information security director at Human Rights Watch, said.
The infection chain commences with the targets receiving suspicious messages on WhatsApp under the pretext of inviting them to a conference and luring the victims into clicking a rogue URL that captured their Microsoft, Google, and Yahoo! login credentials.
These phishing pages are also capable of orchestrating adversary-in-the-middle (AiTM) attacks, thereby making it possible to breach accounts that are secured by two-factor authentication (2FA) other than a hardware security key.
15 of the targeted high-profile individuals are confirmed to have received the same WhatsApp messages between September 15 and November 25, 2022, the international non-governmental organization said.
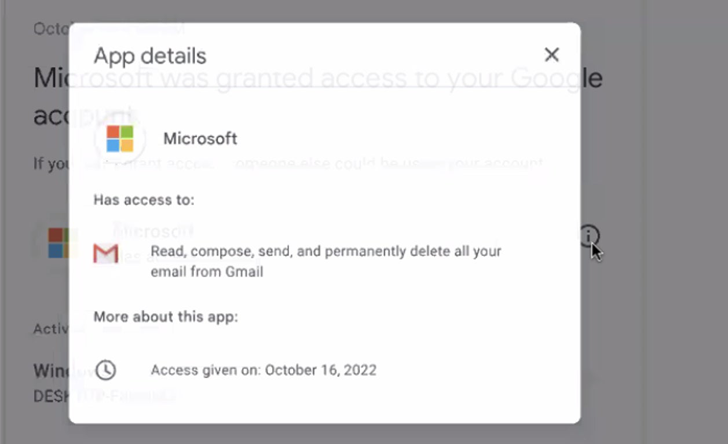
HRW further pointed out inadequacies in Google’s security protections, as the victims of the phishing attack “did not realize their Gmail accounts had been compromised or a Google Takeout had been initiated, in part because the security warnings under Google’s account activity do not push or display any permanent notification in a user’s inbox or send a push message to the Gmail app on their phone.”
The option to request data from Google Takeout lines up with a .NET-based program called HYPERSCRAPE that was first documented by Google’s Threat Analysis Group (TAG) earlier this August, although HRW said it could not confirm if the tool was indeed employed in this specific incident.
The attribution to APT42 is based on overlaps in the source code of the phishing page with that of another spoofed registration page that, in turn, was associated to a credential theft attack mounted by an Iran-nexus actor (aka TAG-56) against an unnamed U.S. think tank.
“The threat activity is highly likely indicative of a broader campaign that makes use of URL shorteners to direct victims to malicious pages where credentials are stolen,” Recorded Future disclosed late last month. “This tradecraft is common among Iran-nexus advanced persistent threat (APT) groups like APT42 and Phosphorus.”
What’s more, the same code has been connected to another domain utilized as part of a social engineering attack attributed to the Charming Kitten group and disrupted by Google TAG in October 2021.
It’s worth pointing out that despite APT35 and APT42’s links to Iran’s Islamic Revolutionary Guard Corps (IRGC), the latter is geared more towards individuals and entities for “domestic politics, foreign policy, and regime stability purposes,” per Mandiant.
“In a Middle East region rife with surveillance threats for activists, it’s essential for digital security researchers to not only publish and promote findings, but also prioritize the protection of the region’s embattled activists, journalists, and civil society leaders,” Ghattas said.
