A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads.
“The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads and downloads,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
“The scripts are designed to fetch files that match specific patterns, suggesting they are waiting for commands or scripts placed in Google Drive or Dropbox.”
The starting point of the attack chain is a phishing email bearing a ZIP archive file, which contains an executable that masquerades as a Microsoft Excel file.

In an interesting twist, the filename makes use of the hidden right-to-left override (RLO) Unicode character (U+202E) to reverse the order of the characters that come after that character in the string.
As a result, the filename “RFQ-101432620247fl*U+202E*xslx.exe” is displayed to the victim as “RFQ-101432620247flexe.xlsx,” thus deceiving them into thinking that they are opening an Excel document.
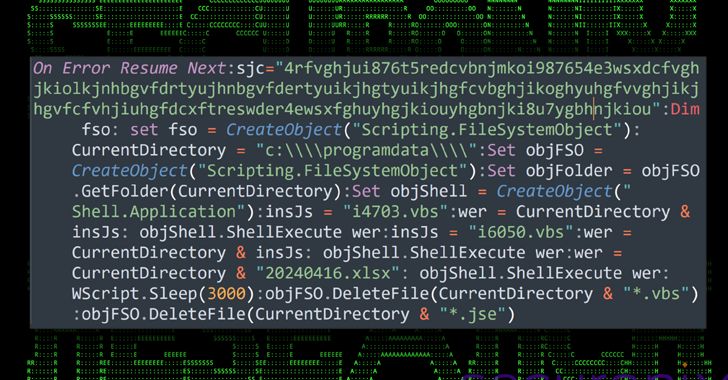
The executable is designed to drop a total of eight payloads, including a decoy Excel file (“20240416.xlsx”) and a heavily obfuscated Visual Basic (VB) Script (“3156.vbs”) that’s responsible for displaying the XLSX file to the user to maintain the ruse and launch two other scripts named “i4703.vbs” and “i6050.vbs.”

Both scripts are used to set up persistence on the Windows host by means of a scheduled task by masquerading them as a Google Chrome browser update task to avoid raising red flags. That said, the scheduled tasks are orchestrated to run two unique VB scripts called “97468.tmp” and “68904.tmp” every minute.
Each of these scripts, in turn, is employed to run two different PowerShell scripts “Tmp912.tmp” and “Tmp703.tmp,” which are used to connect to an actor-controlled Dropbox and Google Drive account and download two more PowerShell scripts referred to as “tmpdbx.ps1” and “zz.ps1”
The VB scripts are then configured to run the newly downloaded PowerShell scripts and fetch more files from the cloud services, including binaries that could be executed depending on the system policies.
“The late-stage PowerShell script zz.ps1 has functionality to download files from Google Drive based on specific criteria and save them to a specified path on the local system inside the ProgramData directory,” the researchers said.
The fact that both the PowerShell scripts are downloaded on-the-fly means they could be modified by the threat actors at will to specify the files that can be downloaded and executed on the compromised host.

Also downloaded via 68904.tmp is another PowerShell script that’s capable of downloading a compressed binary and running it directly from memory in order to maintain network connection to the attacker’s command-and-control (C2) server.
The development is once again a sign that threat actors are increasingly misusing legitimate services to their advantage and fly under the radar.
“This approach follows a common thread where threat actors manage to infect and persist onto compromised systems while maintaining to blend into regular background network noise,” the researchers said.
“By embedding malicious scripts within seemingly innocuous cloud platforms, the malware not only ensures sustained access to targeted environments but also utilizes these platforms as conduits for data exfiltration and command execution.”