Microsoft’s threat intelligence division on Wednesday assessed that a subgroup of the Iranian threat actor tracked as Phosphorus is conducting ransomware attacks as a “form of moonlighting” for personal gain.
The tech giant, which is monitoring the activity cluster under the moniker DEV-0270 (aka Nemesis Kitten), said it’s operated by a company that functions under the public aliases Secnerd and Lifeweb, citing infrastructure overlaps between the group and the two organizations.
“DEV-0270 leverages exploits for high-severity vulnerabilities to gain access to devices and is known for the early adoption of newly disclosed vulnerabilities,” Microsoft said.

“DEV-0270 also extensively uses living-off-the-land binaries (LOLBINs) throughout the attack chain for discovery and credential access. This extends to its abuse of the built-in BitLocker tool to encrypt files on compromised devices.”
The use of BitLocker and DiskCryptor by Iranian actors for opportunistic ransomware attacks came to light earlier this May, when Secureworks disclosed a set of intrusions mounted by a threat group it tracks under the name Cobalt Mirage with ties to Phosphorus (aka Cobalt Illusion) and TunnelVision.
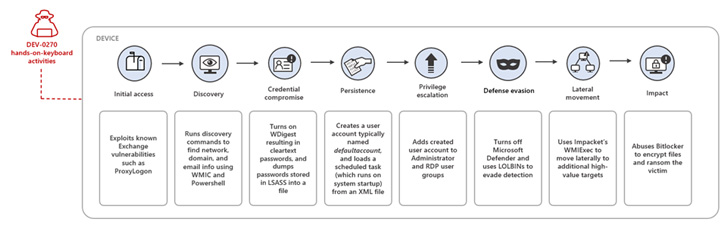
DEV-0270 is known to scan the internet to find servers and devices susceptible to flaws in Microsoft Exchange Server, Fortinet FortiGate SSL-VPN, and Apache Log4j for obtaining initial access, followed by network reconnaissance and credential theft activities.
Access to the compromised network is achieved by establishing persistence via a scheduled task. DEV-0270 then escalates privileges to the system level, allowing it to conduct post-exploitation actions such as disabling Microsoft Defender Antivirus to evade detection, lateral movement, and file encryption.

“The threat group commonly uses native WMI, net, CMD, and PowerShell commands and registry configurations to maintain stealth and operational security,” Microsoft said. “They also install and masquerade their custom binaries as legitimate processes to hide their presence.”
Users are recommended to prioritize patching of internet-facing Exchange servers to mitigate risk, restrict network appliances like Fortinet SSL-VPN devices from making arbitrary connections to the internet, enforce strong passwords, and maintain regular data backups.
