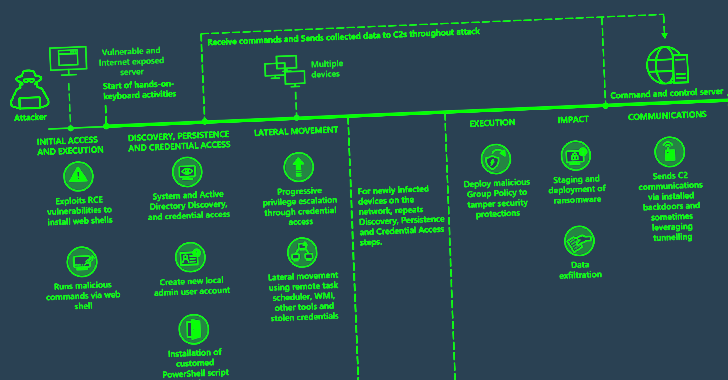
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft said.
The tech giant’s threat intelligence team said it observed both Mango Sandstorm (Mercury) and Mint Sandstorm (Phosphorus) weaponizing CVE-2023-27350 in their operations to achieve initial access.
“This activity shows Mint Sandstorm’s continued ability to rapidly incorporate [proof-of-concept] exploits into their operations,” Microsoft said in a series of tweets.
On the other hand, CVE-2023-27350 exploitation activity associated with Mango Sandstorm is said to be on the lower end of the spectrum, with the state-sponsored group “using tools from prior intrusions to connect to their C2 infrastructure.”

It’s worth noting that Mango Sandstorm is linked to Iran’s Ministry of Intelligence and Security (MOIS) and Mint Sandstorm is said to be associated with the Islamic Revolutionary Guard Corps (IRGC).
The ongoing assault comes weeks after Microsoft confirmed the involvement of Lace Tempest, a cybercrime gang that overlaps with other hacking groups like FIN11, TA505, and Evil Corp, in abusing the flaw to deliver Cl0p and LockBit ransomware.
CVE-2023-27350 (CVSS score: 9.8) relates to a critical flaw in PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.
A patch was made available by PaperCut on March 8, 2023. Trend Micro’s Zero Day Initiative (ZDI), which discovered and reported the issue, is expected to release more technical information about it on May 10, 2023.
Cybersecurity firm VulnCheck, last week, published details on a new line of attack that can circumvent existing detections, enabling adversaries to leverage the flaw unimpeded.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
With more attackers jumping in on the PaperCut exploitation bandwagon to breach vulnerable servers, it’s imperative that organizations move quickly to apply the necessary updates (versions 20.1.7, 21.2.11, and 22.0.9 and later).
The development also follows a report from Microsoft which revealed that Iranian threat actors in Iran are increasingly relying on a new tactic that combines offensive cyber operations with multi-pronged influence operations to “fuel geopolitical change in alignment with the regime’s objectives.”
The shift coincides with an increased tempo in adopting newly reported vulnerabilities, the use of compromised websites for command-and-control to better conceal the source of attacks, and harnessing custom tooling and tradecraft for maximum impact.