A previously undocumented threat actor dubbed Sandman has been attributed to a set of cyber attacks targeting telecommunic koation providers in the Middle East, Western Europe, and the South Asian subcontinent.
Notably, the intrusions leverage a just-in-time (JIT) compiler for the Lua programming language known as LuaJIT as a vehicle to deploy a novel implant called LuaDream.
“The activities we observed are characterized by strategic lateral movement to specific targeted workstations and minimal engagement, suggesting a deliberate approach aimed at achieving the set objectives while minimizing the risk of detection,” SentinelOne security researcher Aleksandar Milenkoski said in an analysis published in collaboration with QGroup.
“The implementation of LuaDream indicates a well-executed, maintained, and actively developed project of a considerable scale.”
Neither the campaign nor its tactics have been correlated with any known threat actor or group, although available evidence points to a cyber espionage adversary with a penchant for targeting the telecom sector across geographies. The attacks were first observed over several weeks in August 2023.
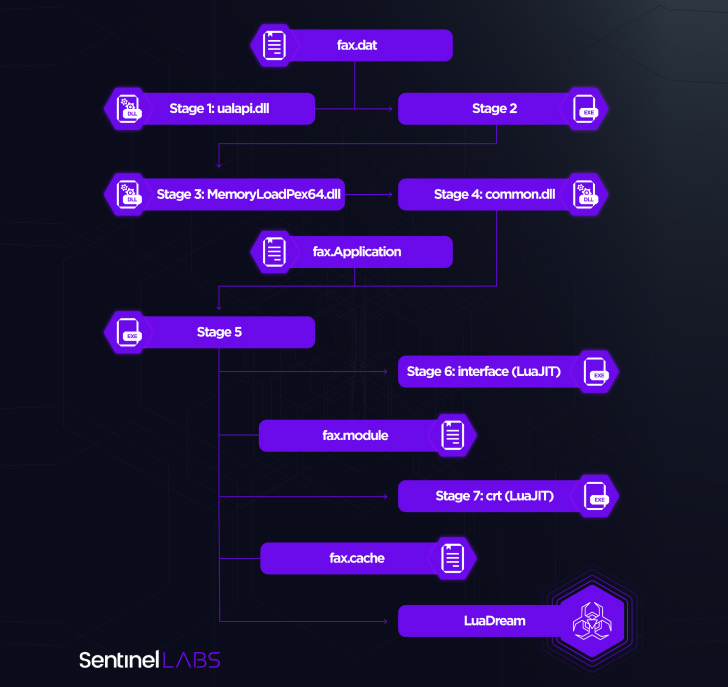
“The LuaDream staging chain is designed to evade detection and thwart analysis while deploying the malware directly into memory,” Milenkoski explained. “LuaDream’s implementation and staging process leverage the LuaJIT platform, the just-in-time compiler for the Lua scripting language. This is primarily to make malicious Lua script code difficult to detect.”

String artifacts contained within the implant’s source code reference June 3, 2022, indicating that the preparatory work has been underway for more than a year.
It’s suspected that LuaDream is a variant of a new malware strain referred to as DreamLand by Kaspersky in its APT trends report for Q1 2023, with the Russian cybersecurity company describing it as employing “the Lua scripting language in conjunction with its Just-in-Time (JIT) compiler to execute malicious code that is difficult to detect.”
The use of Lua is something of a rarity in the threat landscape, having been previously observed in three different instances since 2012: Flame, Animal Farm (aka SNOWGLOBE), and Project Sauron.
The exact mode of initial access remains unclear, but it has been observed stealing administrative credentials and conducting reconnaissance to breach workstations of interest and ultimately deliver LuaDream.
A modular, multi-protocol backdoor with 13 core and 21 support components, LuaDream is primarily designed to exfiltrate system and user information as well as manage attacker-provided plugins that expand on its features, such as command execution. It also features various anti-debugging capabilities to evade detection and thwart analysis.
Command-and-control (C2) communication is accomplished by establishing contact with a domain named “mode.encagil[.]com” using the WebSocket protocol. But it can also listen for incoming connections over TCP, HTTPS, and QUIC protocols.
The core modules implement all of the aforementioned features, while the support components are responsible for augmenting the backdoor’s capabilities to await connections based on the Windows HTTP server API and execute commands.
“LuaDream stands as a compelling illustration of the continuous innovation and advancement efforts that cyber espionage threat actors pour into their ever-evolving malware arsenal,” Milenkoski said.
The disclosure coincides with a parallel report from SentinelOne which detailed sustained strategic intrusions by Chinese threat actors in Africa, including those aimed at telecommunication, finance and government sectors in Africa, as part of activity clusters dubbed BackdoorDiplomacy, Earth Estries, and Operation Tainted Love.
Level-Up SaaS Security: A Comprehensive Guide to ITDR and SSPM
Stay ahead with actionable insights on how ITDR identifies and mitigates threats. Learn about the indispensable role of SSPM in ensuring your identity remains unbreachable.
Supercharge Your Skills
The goal, the company said, is to extend influence throughout the continent and leverage such offensives as part of its soft power agenda.
SentinelOne said it detected a compromise of a telecommunications entity based in North Africa by the same threat actor behind Operation Tainted Love, adding the timing of the attack aligned with the organization’s private negotiations for further regional expansion.
“Targeted intrusions by the BackdoorDiplomacy APT and the threat group orchestrating Operation Tainted Love indicate a level intention directed at supporting [China in its efforts to] shape policies and narratives aligned with its geostrategic ambitions, establishing itself as a pivotal and defining force in Africa’s digital evolution,” security researcher Tom Hegel said.
It also comes days after Cisco Talos revealed that telecommunication service providers in the Middle East are the target of a new intrusion set dubbed ShroudedSnooper that employs a set of stealthy backdoors called HTTPSnoop and PipeSnoop.