Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that’s employed by the North Korean state-sponsored actor known as ScarCruft.
“RokRAT is a sophisticated remote access trojan (RAT) that has been observed as a critical component within the attack chain, enabling the threat actors to gain unauthorized access, exfiltrate sensitive information, and potentially maintain persistent control over compromised systems,” ThreatMon said.
ScarCruft, active since at least 2012, is a cyber espionage group that operates on behalf of the North Korean government, exclusively focusing on targets in its southern counterpart.
The group is believed to be a subordinate element within North Korea’s Ministry of State Security (MSS). Attack chains mounted by the group have leaned heavily on social engineering to spear-phish victims and deliver payloads onto target networks.
This includes exploiting vulnerabilities in Hancom’s Hangul Word Processor (HWP), a productivity software widely used by public and private organizations in South Korea, to deliver its signature malware dubbed RokRAT.
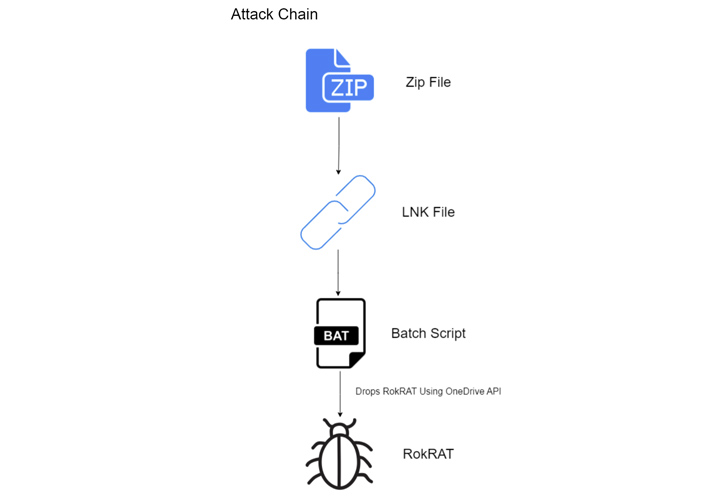
The Windows backdoor, also called DOGCALL, is actively developed and maintained, and has since been ported to other operating systems such as macOS and Android.
Recent spear-phishing attacks, as evidenced by the AhnLab Security Emergency response Center (ASEC) and Check Point, have used LNK files to trigger multi-stage infection sequences that eventually result in the deployment of the RokRAT malware.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
Save My Seat!
RokRAT allows the adversary to harvest system metadata, take screenshots, execute arbitrary commands received from a remote server, enumerate directories, and exfiltrate files of interest.
The development comes as ASEC disclosed a ScarCruft attack that leverages a Windows executable masquerading as a Hangul document to drop malware that is configured to contact an external URL every 60 minutes.
“The URL registered in the task scheduler appears to be a normal homepage, but it contains a web shell,” ASEC noted.
