Entities located in East and Southeast Asia as well as Ukraine have been targeted at least since 2020 by a previously undocumented subgroup of APT41, a prolific Chinese advanced persistent threat (APT).
Cybersecurity firm Trend Micro, which christened the espionage crew Earth Longzhi, said the actor’s long-running campaign can be split into two based on the toolset deployed to attack its victims.
The first wave from May 2020 to February 2021 is said to have targeted government, infrastructure, and healthcare industries in Taiwan and the banking sector in China, whereas the succeeding set of intrusions from August 2021 to June 2022 infiltrated high-profile victims in Ukraine and several countries in Asia.
This included defense, aviation, insurance, and urban development industries in Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine.
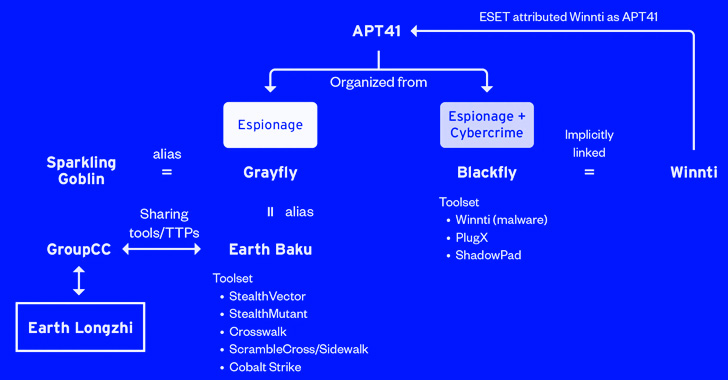
The victimology patterns and the targeted sectors overlap with attacks mounted by a distinct sister group of APT41 (aka Winnti) known as Earth Baku, the Japanese cybersecurity company added.
Some of Earth Baku’s malicious cyber activities have been tied to groups called by other cybersecurity firms ESET and Symantec under the names SparklingGoblin and Grayfly, respectively.
“SparklingGoblin’s Tactics, Techniques and Procedures (TTPs) partially overlap with APT41 TTPs,” ESET researcher Mathieu Tartare previously told The Hacker News. “Grayfly’s definition given by Symantec seems to (at least partially) overlap with SparklingGoblin.”
Now Earth Longzhi adds to another piece in the APT41 attack puzzle, what with the actor also sharing links to a third subgroup dubbed GroupCC (aka APT17, Aurora Panda, or Bronze Keystone).
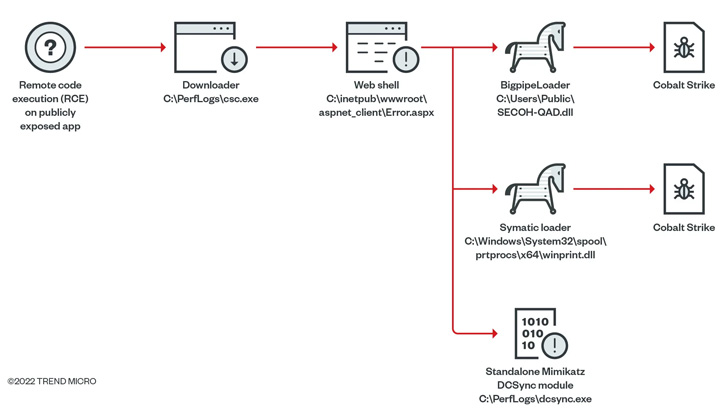
Attacks orchestrated by the hacker group leverage spear-phishing emails as the initial entry vector. These messages are known to embed password-protected archives or links to files hosted on Google Drive that, when opened, launches a Cobalt Strike loader dubbed CroxLoader.
In some cases, the group has been observed weaponizing remote code execution flaws in publicly exposed applications to deliver a web shell capable of dropping a next-stage loader referred to as Symatic that’s engineered to deploy Cobalt Strike.
Also put to use as part of its post-exploitation activities is an “all in one tool,” which combines several publicly available and custom functions in one package and is believed to have been available since September 2014.
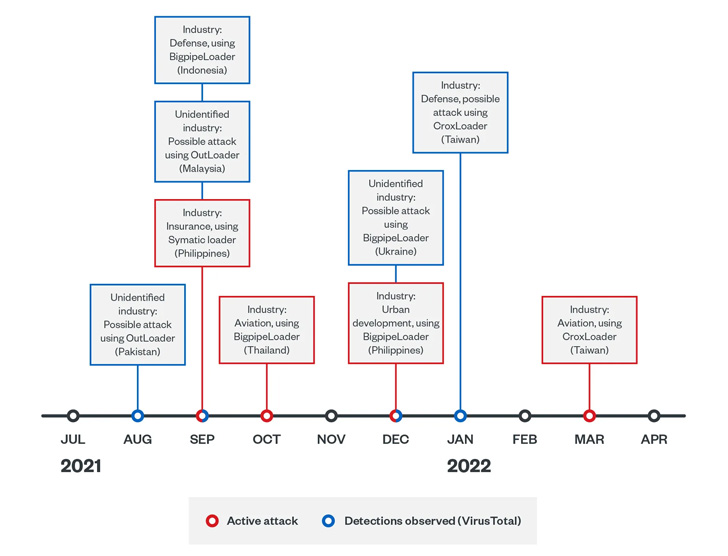
The second series of attacks initiated by Earth Longzhi follow a similar pattern, the main difference being the use of different Cobalt Strike loaders named CroxLoader, BigpipeLoader, and OutLoader to drop the red team framework on infected hosts.
The recent attacks further stand out for the use of bespoke tools that can disable security software, dump credentials using a modified version of Mimikatz, and leverage flaws in the Windows Print Spooler component (i.e., PrintNightmare) to escalate privileges.

What’s more, incapacitating the installed security solutions is pulled off by a method called bring your own vulnerable driver (BYOVD), which entails the exploitation of a known flaw in the RTCore64.sys driver (CVE-2019-16098).
This is carried out using ProcBurner, a tool for killing specific running processes, while another custom malware called AVBurner is used to unregister the endpoint detection and response (EDR) system by removing process creation callbacks – a mechanism that was detailed by a security researcher who goes by the alias brsn in August 2020.
It’s worth noting the outdated version of the RTCore64.sys driver, which still has a valid digital signature, has been put to use by multiple threat actors like BlackByte and OldGremlin over the past few months.
“[Earth Longzhi’s] target sectors are in industries pertinent to Asia-Pacific countries’ national security and economies,” the researchers said. “The activities in these campaigns show that the group is knowledgeable on red team operations.”
“The group uses social engineering techniques to spread its malware and deploy customized hack tools to bypass the protection of security products and steal sensitive data from compromised machines.”